Scareware scammers hijack Twitter trending topics
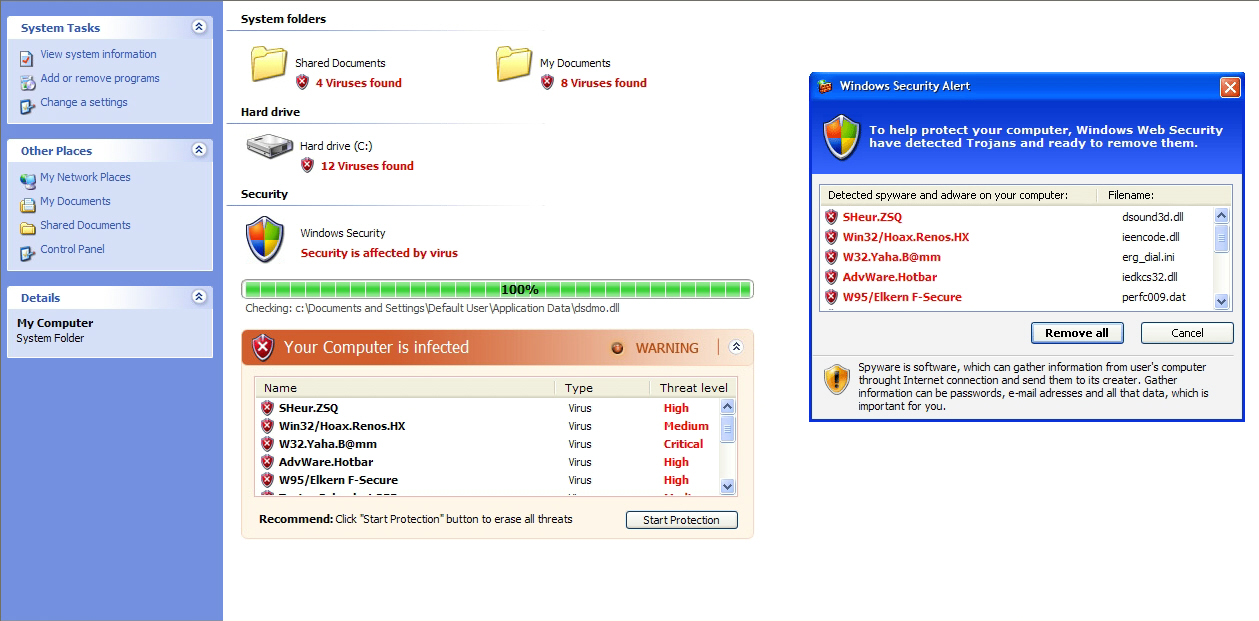
Hundreds of tweets using four different URL shortening services are currently spammed through the automatically registered Twitter accounts, relying on a pseudo-random text generation using Twitter's trending topics.
This isn't the first time (Cybercriminals hijack Twitter trending topics to serve malware) scareware scammers abuse Twitter, and definitely not the last. However, how are the scammers capable of achieving this automation (Commercial Twitter spamming tool hits the market), with Twitter now relying on reCAPTCHA for account registration purposes, a practice which is supposed to limit the automatic abuse of the service?
This outsourcing approach is in fact so successful, that the companies offering these services now offer API keys to commercial spamming vendors that were once on the verge of irrelevance due to the mass adoption of CAPTCHA authentication, which they were unable to automatically recognize.
- Go through related posts: The ultimate guide to scareware protection; Does Twitter's malware link filter really work?; Commercial Twitter spamming tool hits the market; Cybercriminals hijack Twitter trending topics to serve malware; French hacker gains access to Twitter’s admin panel; Spammers harvesting emails from Twitter - in real time; Twitter hit by multiple variants of XSS worm; Koobface worm joins the Twittersphere
Deeper analysis of the campaign reveals a connection to a well-known Ukrainian cybercrime enterprise that was also responsible for the recent malvertising attack at the New York Times, as well as the Bahama botnet facilitating click-fraud uncovered by ClickForensics.