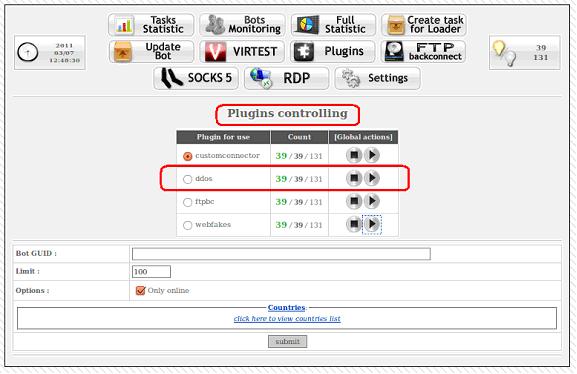
SpyEye gets new DDoS functionality
Researchers from RSA's FraudAction Research Lab are reporting on a recently discovered new DDoS module within the popular crimeware SpyEye. Based on various conversations within the cybercrime ecosystem -- I also get a mention there -- the primary application of the plugin would be to attack legitimate sites such as Abuse.ch's ZeusTracker, and the SpyEye tracker, a community-driven services aiming to track crimeware campaigns.
The DDoS plugin currently offers SYN Flood; UDP Flood and Slowloris Flood, modes of operation.
Next to the new module, the researchers have also observed a new trend aiming to generate additional noise and poison the results offered by the two services. By including legitimate sites next to the malicious one, cybercriminals aim to make it harder for the service to distinguish between legitimate and purely malicious ones:
This means that all the credentials collected by the Trojan from SpyEye bots, including screenshots, username and password combinations, and stolen certificates and cookies, will be sent to port 443 of the legitimate websites, like the ones mentioned above. When abuse.ch’s Trackers analyze SpyEye variants like the ones we traced, legitimate website domains will be classified as those variants’ communication points. These, in turn, will show up in the SpyEye Tracker blocklist, and serve to diminish its credibility.
This isn't (See: Crimeware tracking service hit by a DDoS attack) the first coordinated attempt to disrupt the operation of the service, and definitely not the last, clearly speaking for its usefulness.