Symantec: Vista's UAC prompts can't always be trusted

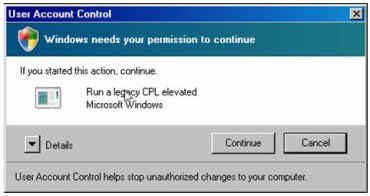
Ollie Whitehouse, a well-known researcher who joined Symantec with the @Stake acquisition, has discovered a scenario where UAC prompts can look like it's coming from Microsoft Windows -- when in fact the user is being asked to authorize admin rights for malicious code.
Whitehouse's discovery, detailed in an entry on Symantec's security response blog, effectively identifies a "chicken and egg situation" where the end user is making a decision based on a false sense of trust.
"The problem with this is that the arbitrary CPL files can be written to areas of the disk that non-administrative users can write to," Whitehouse explained.
He describes the following attack scenario:
- The user gets infected by malicious code running as a restricted user – Trojan or exploit are two likely vectors
- This malicious code drops a malicious CPL file to disk in a location that the restricted user can write to
- The malicious code then calls RunLegacyCPLElevated.exe with the malicious CPL as a parameter
- The user is presented with a UAC prompt that claims that Microsoft Windows needs to elevate permissions and not a third party application
- The user authorizes and the malicious code obtains administrative privileges
When Whitehouse approached Microsoft with this issue, he said the company pointed him to a best-practices document (.doc) that makes it clear that UAC prompts should not be viewed as a security boundary because they don't offer direct protection.
This, in Whitehouse's mind, is not an acceptable response. "I believe Microsoft needs to start to take these a little more seriously than just pointing at best practice guidelines that have the same likelihood (not much) of being implemented or followed as telling people not to open arbitrary executables attached to e-mails," he argued.
[NOTE: Symantec plans to create technology that replaces UAC in Windows Vista so it's fair to say that these Symantec warnings may be tied to the the fierce rivalry between the two companies].
At this year's Black Hat Federal conference in Washington, DC, Whitehouse is on tap to give a two-part presentation on Microsoft's GS implementation and usage and the way ASLR (address space layout randomization) is implemented in Windows Vista.