SYNful Knock: Cisco router malware in the wild

Update, September 16: Some security problems happen because of security holes that have been hiding for years, like OpenSSL's Heartbleed. Others because a program is so defective it can never really be secured: Adobe Flash--164 bugs so far this year. Then, there's PEBCAK, which is short for "Problem Exists Between Chair And Keyboard." That's the kind of problem behind Cisco routers' SYNful Knock.
Is it breaking into a house when you give the crook the key?
I don't know about that, but I do know that once they're in the router, they can use this backdoor to replace your Cisco router operating system with a stealthy and malicious version of the router's firmware image. This can then be hid within your network. Once there, this customizable and modular malware can be updated. Adding salt to your network wound, this backdoor can be difficult to detect because it uses non-standard packets as a form of pseudo-authentication.
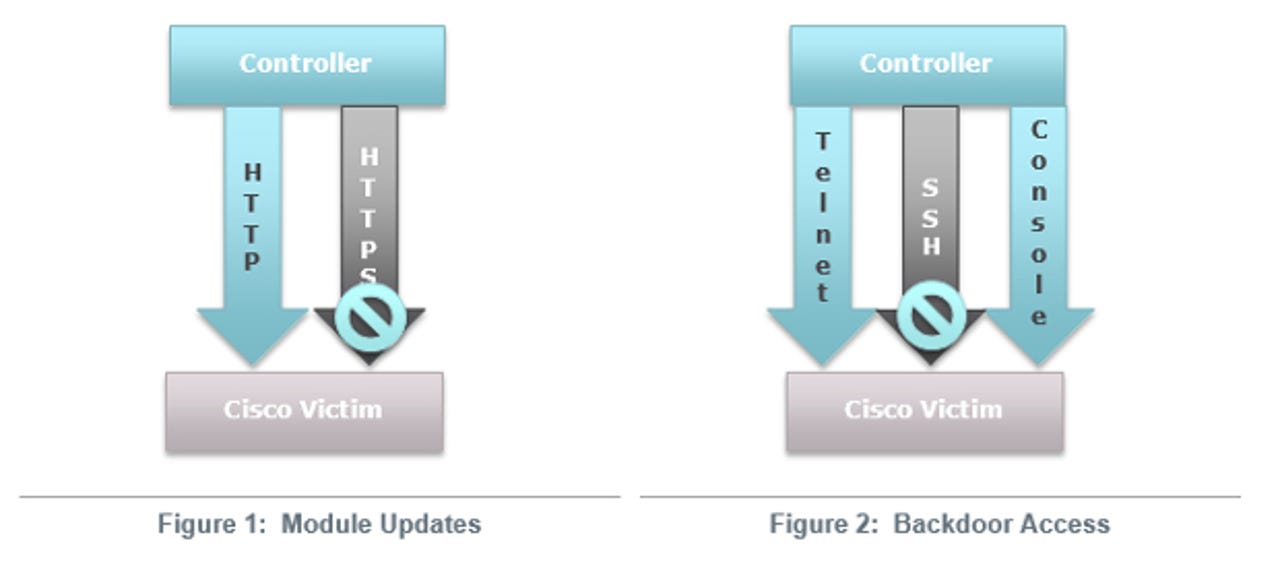
According to FireEye, the backdoor gives attackers "unrestricted access using a secret backdoor password. Each of the modules are enabled via the HTTP protocol (not HTTPS), using a specifically crafted TCP packets sent to the routers interface. The packets have a nonstandard sequence and corresponding acknowledgment numbers. The modules can manifest themselves as independent executable code or hooks within the routers IOS that provide functionality similar to the back-door password. The back-door password provides access to the router through the console and Telnet."
Security
The one "good" thing about this hacked IOS kernel is that its authors were sloppy. Attackers, at this time, cannot access the backdoor password via secured SSH or HTTPS sessions. Thus, simply blocking access to the router via non-encrypted channels will keep hackers from getting at its backdoor.
However, just because the program is relatively weak now doesn't mean attackers can't "upgrade" it. In the meantime, your network will still be wide open to a variety of data raids and loading other malware programs into your networked systems.
You can check to see if your routers have been infected by using Snort with the new Cisco Talos Snort Rule SID:36054.
A group of academics have searched the IPv4 Internet with ZMap for infected Cisco routers. To date, they've found "79 hosts displaying behavior consistent with the SYNful Knock implant."
If you have an infected router, take it out of service and replace it with a clean one. Then, update the router with a verified IOS image.
Finally, fire the network administrators who allowed this to happen. There is no excuse for this kind of sloppiness.
Related Stories: