Target's data breach: No, really. It gets even worse.

There appears to be no end in sight for just how bad the unprecedented hack attack at Target was last holiday season.
And now it looks like Target was not the lone, er, target, in this particular sting.
We've already heard about a similar style attack on the point-of-sale hardware infrastructure at high-end department store chain Neiman Marcus.
Now Reuters is reporting that cyber intelligence firm IntelCrawler has unearthed evidence pointing toward at least six ongoing schemes at U.S. merchants with credit card processing systems plagued by the same type of malicious software.
The news agency's report did not specify the other retailers afflicted by the attack -- only that the infected systems were at stores with locations in California and New York.
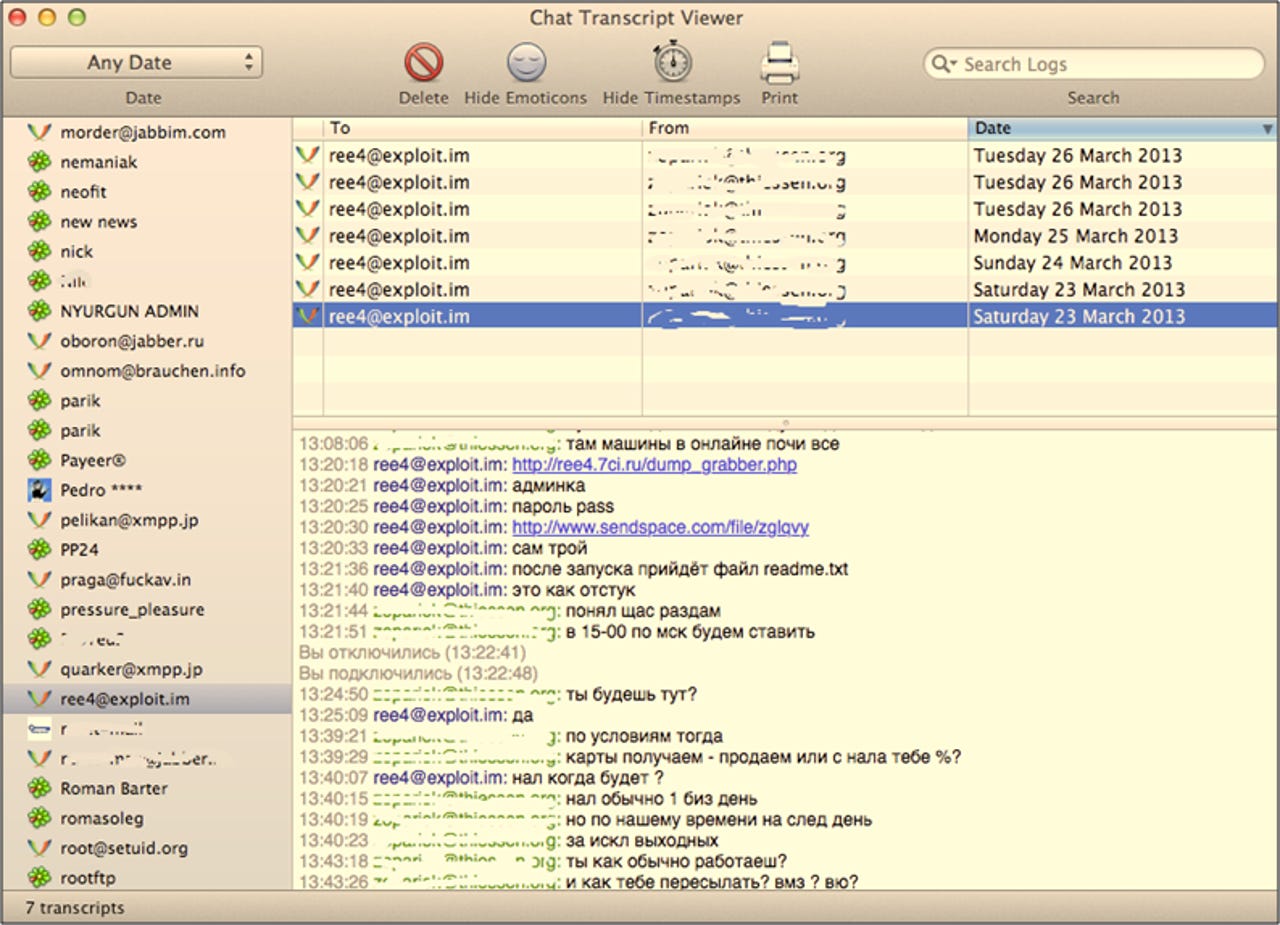
IntelCrawler followed up with a related memo published to its site on Friday, detailing evidence pointing to who could turn out to be the author of the BlackPOS malware that successfully lifted personal data from the magentic strips on the backs of credit cards belonging to more than 70 million Target shoppers between Thanksgiving and mid-December.
According to IntelCrawler's sources, the malware has been tested out and infected point-of-sale hardware across Australia and Canada as well as the United States.
The same dates the detailed information and reverse engineering report were shared with Visa and several major US banks, after which US LEA released internal notification for financial industry about that. The bad actor was pretty opened for trading this malware for 2 000 USD or by receiving 50% from selling of all intercepted credit cards by his customer through Liberty Reserve.
The full report and associated screenshots are available on IntelCrawler's website now, with the hypothesis that the "the age of BlackPOS malware author is close to 17 years old and the first sample of it was created in March 2013."
Image via IntelCrawler