The average ransom demand for a REvil ransomware infection is a whopping $260,000

In today's crowded ransomware landscape, the REvil (Sodinokibi) ransomware gang rules supreme, dwarfing any other similar ransomware operations.
Run as a Ransomware-as-a-Service (RaaS), the REvil gang rents its ransomware strain to other criminal groups.
These groups, known as REvil affialiates, are solely responsible for distributing the ransomware to victims through the channels they prefer, and then ask for the ransom demand they see fit, based on the number of computers they manage to infect on a company's network.
Due to this multi-actor setup and REvil's configurability, keeping an eye on all REvil RaaS operations and affiliate distribution campaigns has always been complicated, requiring a massive effort in terms of both manpower and working hours.
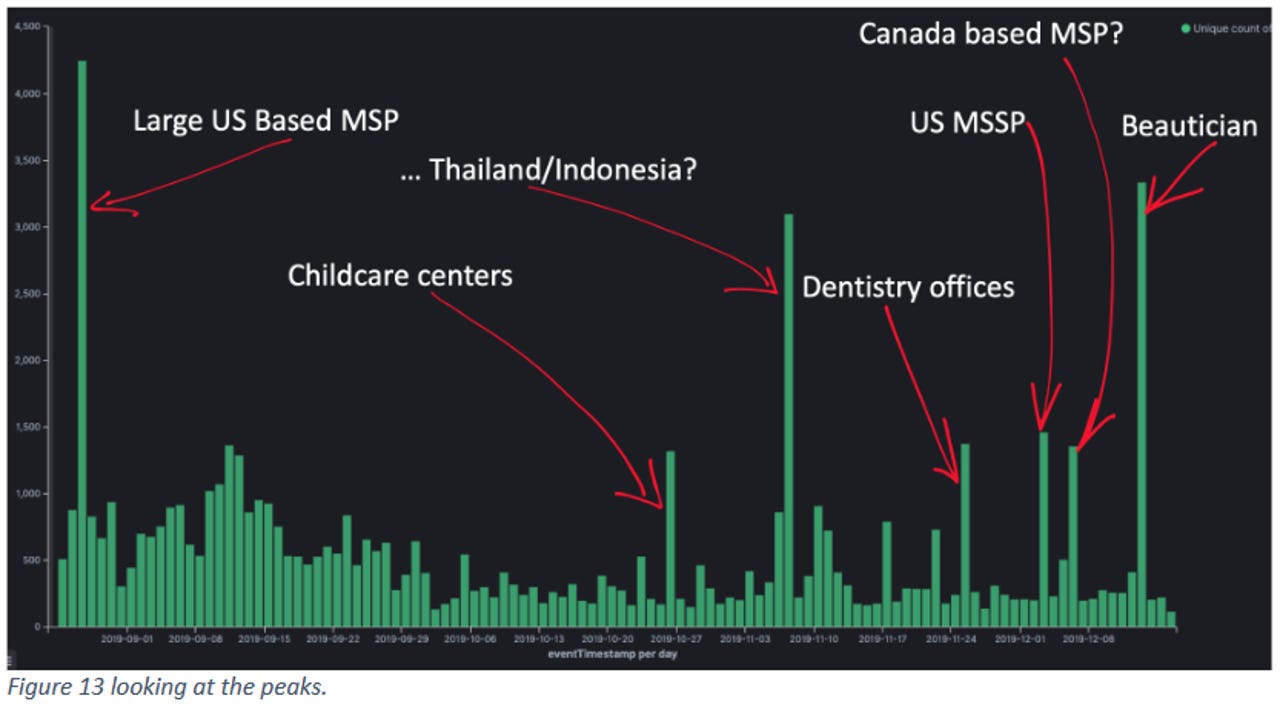
Researcher sinkhole REvil RaaS backend
However, in a report published today and shared with ZDNet, the security team at KPN, a Dutch telecommunications provider, said it was able to sinkhole and intercept the communications between REvil-infected computers and the REvil ransomware's command-and-control (C&C) servers.
KPN researchers say this allowed them to obtain unique insights into the operations of the REvil RaaS, such as the number of active infections, the number of infected computers per attack, and even the sum of money (ransom) hackers requested from victims in each recent incident.
After compiling all their data, the KPN team says that in the past five months during which they've been tracking REvil activities, they've seen more than 150,000 unique infections across all over the globe.
These 150,000 infected computers were linked back to only 148 samples of REvil ransomware strains. Seeing that REvil strains are usually deployed on per-case basis, each strain represented a successful infection of a company's network.
"Some of the attacks are on a huge scale, encrypting over 3000 unique systems in one attack," the KPN team said. "Some of these attacks where discussed in the news, but many companies remained silent."
But besides knowing how many companies and computers REvil operators infected in recent months, KPN researchers say they were also able to determine how much money the hackers attempted to extort from their victims.
According to their findings, KPN says they were able to determine that REvil affiliates requested ransom demands totalling more than $38 million over the past few months, with an average of $260,000 per infected company.
Of the 148 samples the KPN team analyzed, 73 samples only encrypted data on one computer only, meaning that REvil affiliates failed to escalate from their entry point and spread to a company's entire network.
In these single infection cases, the average ransom demand was $48,000, smaller than the $260,000 average, but still far larger than the usual $1,000 or $2,000 that regular ransomware strains tend to request from home users.
However, a much larger ransom demand average was found in cases where the REvil affiliates were successful in expanding their access from the initial foothoold to a company's entire internal network.
For these 75 REvil samples that appeared to have infected multiple workstations inside a company's network, the average ransom demand was $470,000 per company, and with many incidents passing the $1 million mark.
It is unclear how many of these ransoms REvil victims paid, but the average ransom demands that KPN managed to extract from the REvil samples are superior than numbers reported by other sources in the cyber-security industry.
For example, according to Coverware, a cyber-security company that helps victims recover from ransomware attacks and sometimes negotiates payments on behalf of the victims, in Q4 of 2019, the average ransom payment increased by 104% to $84,116, up from $41,198 in Q3, 2019.
Comparing the two numbers -- $260,000 and $84,116 -- we see that the REvil gang is attempting to extort payments from victims far larger than what most other ransomware gangs are requesting.
One of the reasons for this might be REvil's excellent PR campaign on underground hacking forums, where the ransomware's creator has often advertised it as a top-tier solution to be used primarily and solely in attacks against large corporate networks, rather than being slinged at home consumers via mundane spam campaigns.