This phishing email uses an unexpected trick to infect PCs with keylogger malware

The lure comes in the form of a Packager Shell Object.
Cybercriminals are targeting a US major financial services provider with malicious emails containing the tools required to install information collecting keylogging software onto the infected systems.
Keylogging enables hackers to see everything that's typed using the keyboard of an infected machine, something which can be exploited to steal information, personal information, and login credentials.
Cybersecurity researchers at Proofpoint note that the attack is very narrow in scope, targeting users in just a single US-based financial services and insurance organisation with malicious emails. Naturally, banks are a high-profile target for cybercriminals who not only see money as a lucrative target, but also view financial institutions as a treasure trove of data to exploit.
Like many phishing threats, the email contains an attachment in the form of a Microsoft Word document, designed to deliver the payload. However, unlike most phishing emails containing malicious attachments, which use macros to avoid detection, this one uses an embedded object in the form of a Visual Basic Script that acts as a downloader for the malware.
"It is a Packager Shell Object. When content like a script is packaged as a Packager Shell Object, it can be opened and executed from within the Microsoft Office file in which it is embedded," says Kevin Epstein, VP of the threat operations center at Proofpoint.
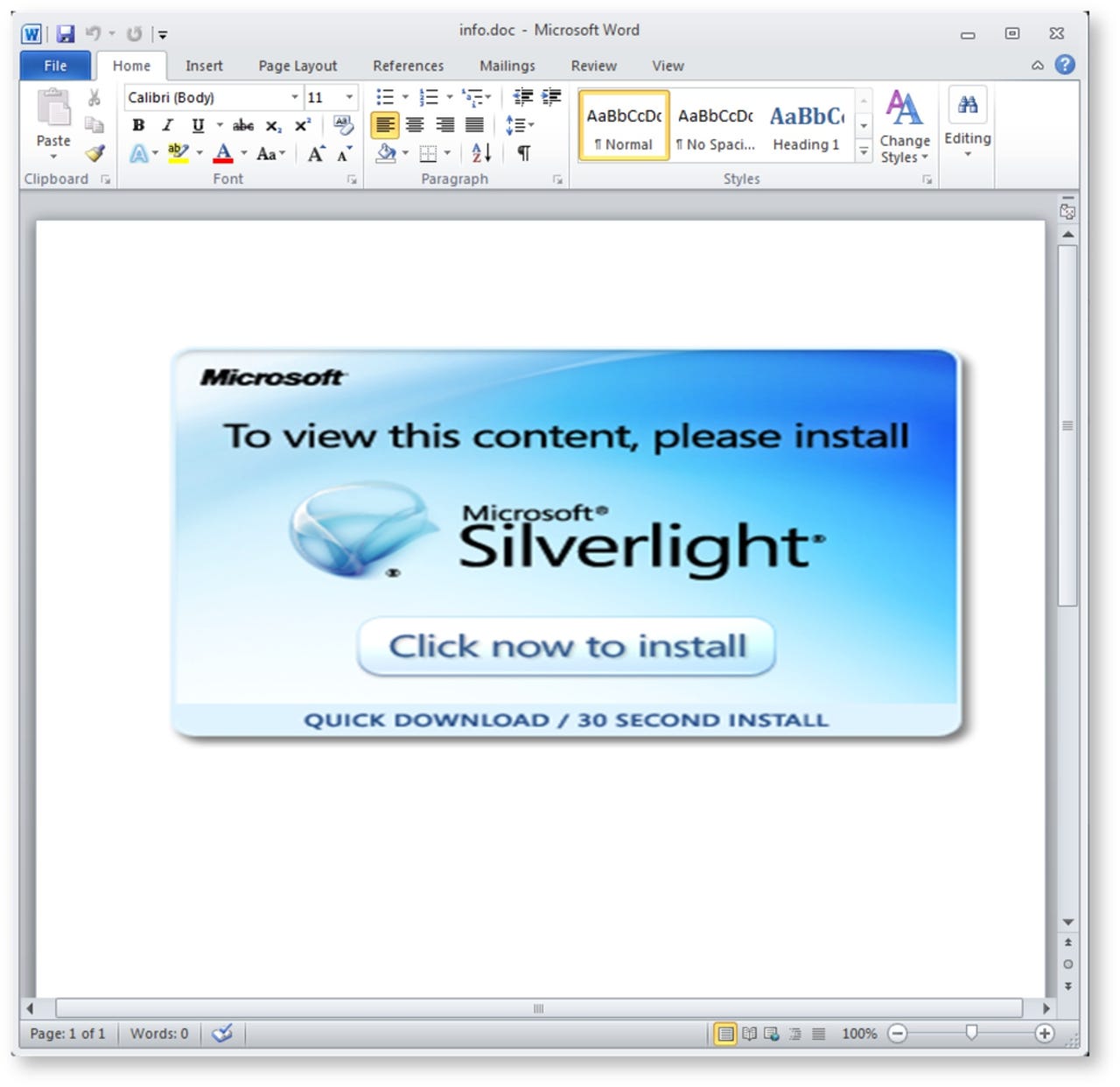
In this instance, the emails sent in this cyberattack include a Microsoft World attachment named "info.doc", which contains an image requesting the user clicks on it to install Microsoft Silverlight in order to view the supposed content of the document.
However, upon closer examination of the image, researchers note that it reveals itself as not a link, but rather a Visual Basic Script file which contains code for keylogging malware which will run when clicked on.
Once installed on an infected system, the malware will log the keystrokes and sends the information to two hard-coded Gmail addresses.
While researchers haven't been able to specifically identify the keylogger being used in this attack, it's written in the Aultolt scripting language and uses tools including Lazagne password recovery to help gather credentials.
There's no indication of who is behind the attacks against the unnamed financial services firm, but researchers indicate the malicious software used was obtained from a public malware repository and uploaded from Estonia. According to Proofpoint, this indicates that the keylogger may have been used in attacks against similar institutions.
Researchers note that while the malware is basic compared to other exploits, the way the keylogger is being delivered to end users represents a shift from the tried and tested method of tricking them into enabling macros.
While Microsoft Office applications can block macros by default, this threat indicates that cyberattacks are very much active in developing new ways to deliver their malicious payloads.
Read more on cybercrime
- Spying is the new hacking: Here's how to fight back
- Odinaff Trojan attacks banks and more, monitoring networks and stealing credentials
- Infographic: How to identify and avoid phishing attacks [TechRepublic]
- Locky ransomware campaign exploits fears of data stolen in OPM hack
- How to use Google's Password Alert tool to thwart phishing attacks [CNET]