Today's leading causes of DDoS attacks

Last fall, we saw the biggest distributed denial of service (DDoS) attack ever. This year, we'll see even bigger ones. According to Akamai's latest State of the Internet Security report, here's what's behind them.
Behind today's DDoS attacks you'll find botnets and they're using the same old techniques hackers have always used to bring down your servers.
First, you should know that while the total DDoS attacks only increased by 4 percent from Q4 2015 to Q4 2016, there was a 140-percent increase in attacks greater than 100Gbps. In short, we're not seeing that many more DDoS assaults, but they are getting much worse.
Security
Of the most recent mega 100Gbps attacks in the last quarter, most of them were directly attributed to the Mirai botnet. The Mirai botnet works by exploiting the weak security on many Internet of Things (IoT) devices. The program finds its victims by constantly scanning the internet for IoT devices, which use factory default or hard-coded usernames and passwords.
It's hard to detect infected IoT gadgets because, unlike PCs, an infected webcam or DVR doesn't show its owner any symptoms. More annoying still, while simply rebooting a device will usually get rid of the Mirai malware, without a firmware update, it's still wide open to being re-infected.
Mirai won't go away anytime soon. Its source code was released last fall and hackers are using it to create their own variants. As James Scott and Drew Spaniel of the Institute of Critical Infrastructure Technology reported in their white paper, Rise of the Machines: The Dyn Attack Was Just a Practice Run, "the Mirai malware offers malicious cyber actors an asymmetric quantum leap in capability; not because of sophistication or any innovative DDoS code, rather it offers a powerful development platform that can be optimized and customized."
Don't get too focused on Mirai. Scott and Spaniel continued: "Mirai will not forever remain the favorite tool of unsophisticated malicious threat actors. In fact, due to a saturated pool of bot victims, script kiddies have already begun adapting the malware to new victim hosts or adopting new malware altogether."
As Akamai noted, last quarter's biggest attack, which topped out at 517Gbps, didn't come from Mirai. Instead, it arose from an older botnet powered by embedded Linux-based BillGates and xor malware/botnet pairing.
Besides, as more and more insecure IoT devices are added to the internet, they create an ever-growing pool of attack resources. Akamai explained, "As vulnerable devices are added to IoT-based botnets, we expect a second surge in botnet capabilities and DDoS attack size."
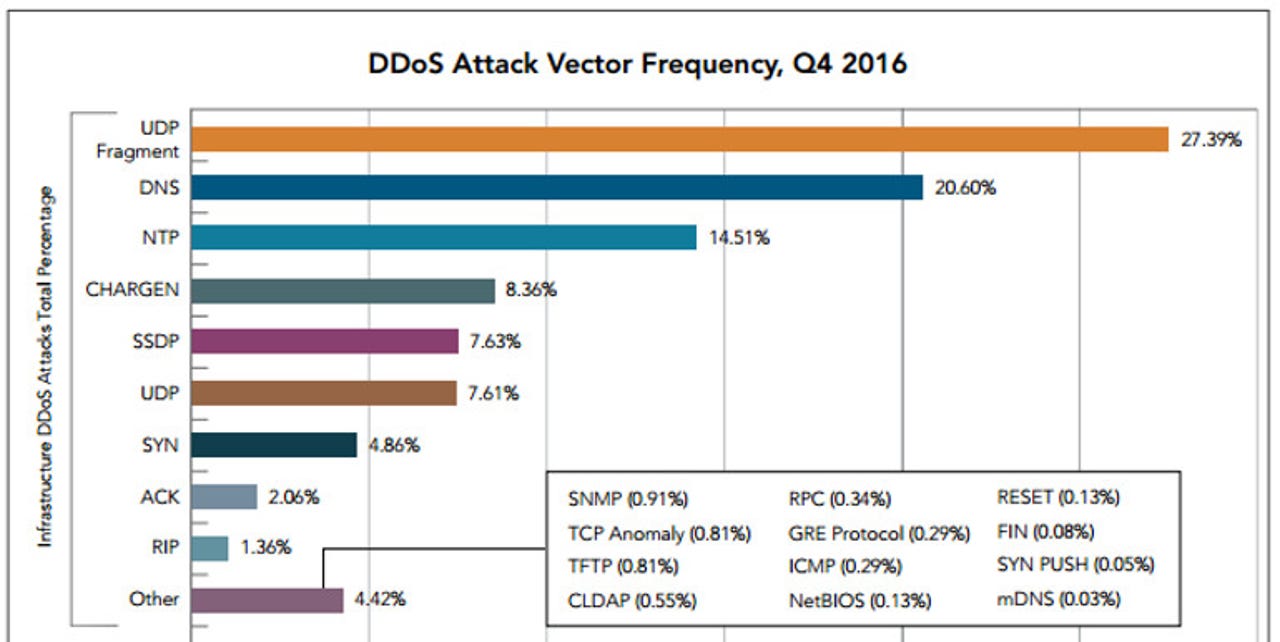
These devices, and older DDoS attack agents use a variety of attack methods. By Akamai's latest count, the top three attack methods are User Datagram Protocol (UDP) fragmentation, 27 percent; Domain Name Server (DNS), 21 percent; and Network Time Protocol (NTP), 15 percent.
Sound familiar? They should. While the primary source of DDoS attacks have become botnets, the methods remain largely the same.
What can be done about this? There are things you can do to protect your servers, but the real answer must come from hardware original equipment manufacturers (OEMs).
Akamai's simple solution is: "IoT devices should ship preconfigured with per-device random passwords or they should require owners to change the password on the initial login."
Simple right? But until consumer electronics vendors start taking security seriously, there will be larger and larger DDoS attacks.
Related Stories: