Tox ransomware owner 'screws up,' offers platform for sale

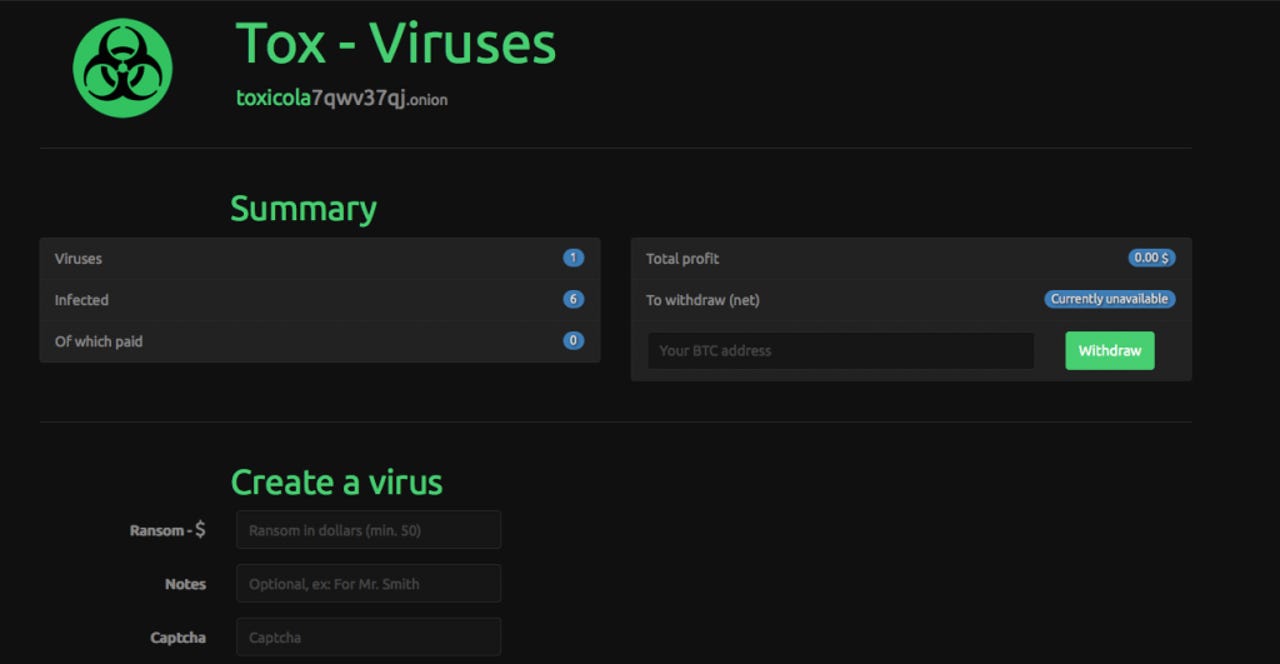
The Tox toolkit gives would-be cybercriminals the option to develop custom ransomware tools with advanced evasion capabilities. In order to detect the malware, additional controls would need to be in place on a PC -- such as HIPS, whitelisting and sandboxing.
However, the kit's enticing feature is its ease of use, as Tox needs only a few custom fields submitted to develop a personalized ransomware platform.
The toolkit can be accessed through the Tor network. When registered for free to use the tool, an executable of about 2MB disguised as a .scr file with custom fields such as the rate of ransom can be created before distribution. The Tox site then tracks install rates and profit. If Tox is downloaded onto a PC, files are encrypted and a ransom in Bitcoin is demanded.
The ease of use proved popular -- but too popular for the owner to cope with.
This week, a post on Pastebin contained a note from the ransomware creator apologizing to Tox users, as well as the promise to release the encryption keys to victims -- unless someone is willing to take the platform off their hands.
Tox was developed roughly one month ago. After two weeks, the ransomware system was uploaded and sent out into the web. In order to drum up interest, the developer posted links to Tox around the Deep web and after only seven days things "exploded," according to the ransomware creator.
Security firms such as McAfee took a recent interest in Tox, and this in turn threw the ransomware platform into the spotlight. It didn't take long before the platform counted over one thousand users and recorded over one thousand infections -- with an average of "more than two hundreds of polling viruses per half-hour."
Featured
However, the last seven days and the ransomware platform's growing popularity have made the creator grow hot under the collar.
"Plan A was to stay quiet and hidden. Well, I think I screwed up," the developer writes. "It's been funny, I felt alive, more than ever, but I don't want to be a criminal."
The situation is "getting too hot for me to handle," the developer says -- who is not a black-hat hacker with years of experience. Instead, they claim they are only a teenage student.
The developer says they want out -- and therefore wishes to sell the platform on to someone else. If there are no takers, in one month the keys will be released and files will be automatically unlocked for Tox's current victims.
Whether there will be a buyer for the ransomware remains to be seen -- but the situation does highlight how quickly the next generation is learning to manipulate code and how easy it can be to launch ransomware platforms online. The developer may be over their head, but still mentions an interesting point concerning the community development of the ransomware platform.
"One last thing: if I really was a team of hardcore hackers, with time and resources, this would have become one the greatest viruses ever.
In these days, in the chat, people helped me testing and debugging the virus, but the most interesting part is that they suggested me how to improve it. I don't think that such a great brainstorming has ever happened in the process of designing a virus. Users were spurred to help me improving the platform, for their own good."
This month, another ransomware kit creator wanted out before ending up behind bars. The alleged creator of the Locker ransomware, known under the alias "Poka Brightminds," said they never planned to publicly release the ransomware and promised to open up the systems' database and release keys to victims. According to Symantec, the creator made only $169 through ransom demands.
Read on: In the world of security