UK university websites hijacked; selling Viagra etc.

A computer security firm has discovered a number of UK colleges and universities with the .ac.uk domain name hijacked and redirected to fake drug stores offering the usual spam-box full of supplies, according to the BBC.
It is believed that the PHP code on the sites was injected with malicious code which redirected them to fake drug stores, so when a user searches certain keywords on Google, the university or college website would appear at the top and be redirected from there. The value of the legitimate site may have boosted link views it is thought.
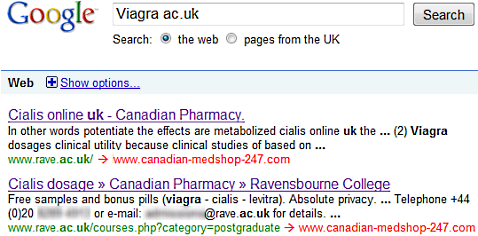
This appears to be a similar, or even perhaps the remnants of a previous assault which hit a number of wider websites last year - including schools and domain names ending in .gov.uk - the UK's government domain name.
Some of these webites can still be found with code injected at this Google search and this one. It is advised you do not click on any further links on the search results.
One student emailed me pointing out that their university had been hacked for months and issues were still arising from it. They were also concerned about their network security and how far this or other security breaches could go into the network.
Good news and bad news, for you my anonymous student friend.
It is good practice to have any public facing website for an organisation totally nucleated away from any internal network structure, including storage spaces and collaboration areas. Take a university website for example. There will be many areas there of which an ordinary member of the public can view the site but will be stonewalled by user authentication procedures when they get too far. This will only be reserved for students and staff.
But with the more internal network exposed - such as accessing read-only file directories offering a wide range of course files or student data - available on the web through a URL, whether it is password protected or not, can lead to dangers there. If the main website gets breached, as from time to time they will do, the behind-the-scenes may not be as safe and secure as you may hope.
Then again, if a website is breached and installs malware locally, you could end up bringing down your entire university network like what happened in Exeter only a few months ago.
I do not envy those who work in network security. The revolver I keep in my desk would make more than a daily appearance I fear.