WannaCry ransomware was the biggest challenge of the year, says cybersecurity centre

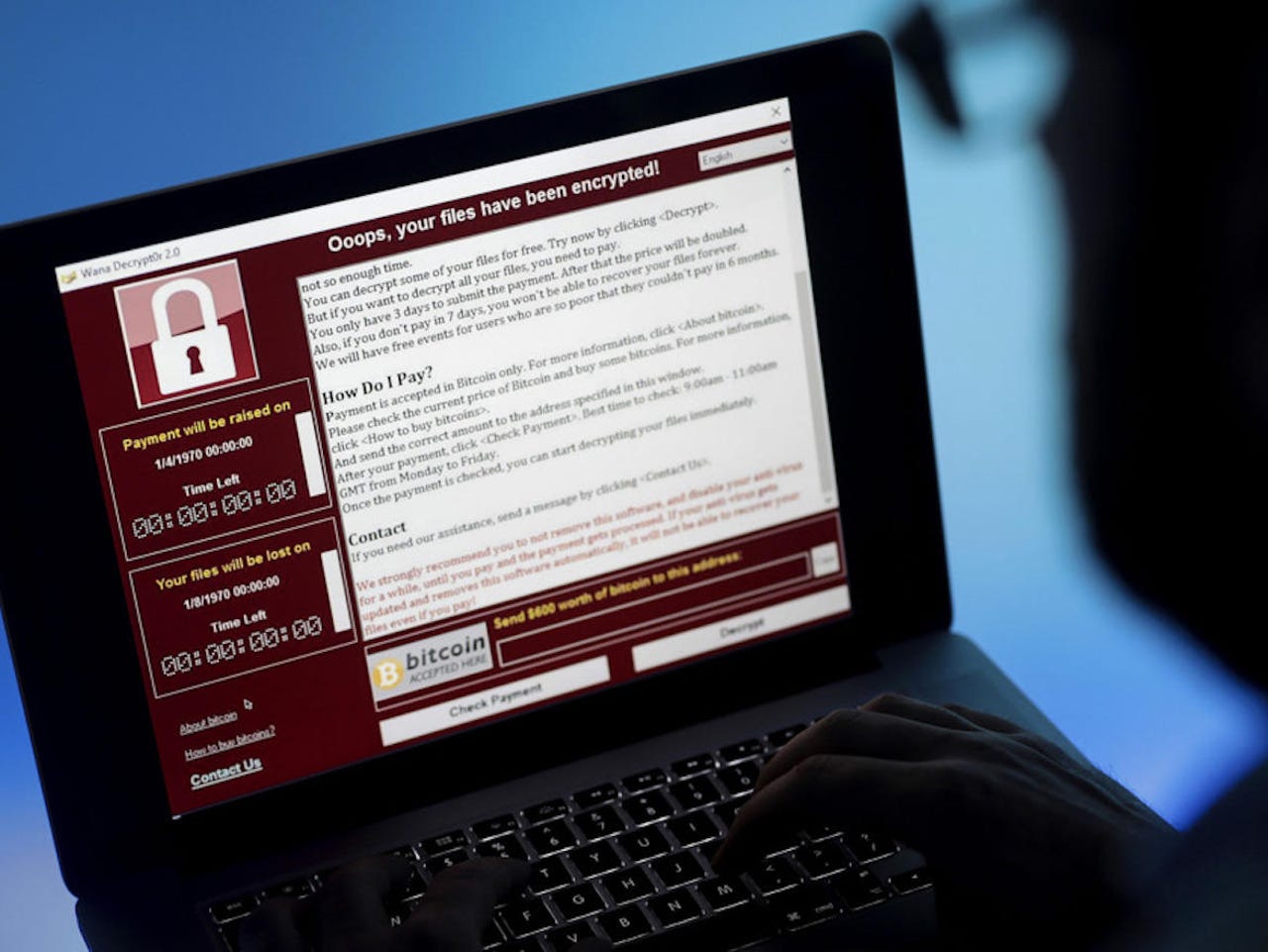
The WannaCry attack warranted a meeting of the government's Cobra crisis committee.
The WannaCry ransomware attack was the biggest test of the year for the UK's new cybersecurity body.
The National Cyber Security Centre's (NCSC) annual review marks a year since it started work, although it was officially opened in February. In those 12 months, the NCSC says 1,131 cyber incidents have been reported to it.
Of those, 590 were classed as significant cyber attacks, ranging from attacks on National Health Service hospitals and the Houses of Parliament, through to attacks on businesses.
Thirty of these incidents were deemed sufficiently serious to require the NCSC, which is part of GCHQ, to coordinate a cross-government response. Of these, the WannaCry attack was considered so significant that it warranted a meeting of the government's Cobra crisis committee.
Other cyberattacks which required a cross-government response included the Tesco Bank hack -- which saw a total of £2.5 million stolen from 9,000 customers -- and June's Petya ransomware outbreak.
The WannaCry epidemic saw ransomware spread with the help of a leaked NSA exploit and infected over 300,000 PCs at major organisations around the globe. The NHS was one of the highest profile victims of the attack, with 47 trusts and foundation trusts affected. The ransomware forced a number of hospitals offline and some took weeks to recover.
The NCSC's response to WannaCry involved a record number of cybersecurity professionals sharing information and NCSC experts deployed to sites which had fallen victim.
The NCSC continues to work with government departments to identify vulnerabilities and which data should be backed up so as to not become irrecoverable should a similar attack occur in future.
See also: Ransomware: An executive guide to one of the biggest menaces on the web
The organisation also led a government review of lessons learned from the incident, including the need for increased collaboration with law enforcement and improving the resilience of NHS networks.
The NCSC continues to investigate who carried out the attack. While the culprit hasn't officially been identified, security services on both sides of the Atlantic suspect the attack was launched by hackers in North Korea.
The NCSC report notes that despite the body's best efforts, it can't prevent every attack. At the same time, it aims to deliver a "world-class incident management service" and ensure all the necessary provisions are in place to react to incidents.
"The threat remains very real and growing -- further attacks will happen and there is much more for us to do," said Ciaran Martin, CEO of the NCSC.
While the report cites WannaCry as the biggest test for the NCSC so far, the body's technical director Ian Levy recently warned that it's likely only a matter of time before an attack which makes WannaCry looks like small fry hits the UK.
Previous and related coverage
GCHQ's new arm will test strategies and schemes for businesses and industry to follow in future.
Gallery: 10 major organizations affected by the WannaCry ransomware attack [TechRepublic]
WannaCry, a ransomware program that has hit hundreds of thousands of machines in the past week, leverages a Windows exploit used by the NSA that was leaked to the internet in April 2017.
READ MORE ON CYBERCRIME
- WannaCry: Why this ransomware just won't die
- 6 tips to avoid ransomware after Petya and WannaCry [TechRepublic]
- GCHQ encourages teenage girls to become cybersecurity professionals of the future
- The global ransomware epidemic is just getting started [CNET]
- Ransomware surges again, as cybercrime-as-a-service becomes mainstream for crooks