Why Windows users should care about malware on Macs

Why is a Windows guy writing so much about malware on Macs? Because it affects me, too.
I have a Mac on my desktop. I use it regularly. I have friends, family members, clients, and professional associates who use Macs. Several of them switched specifically because they believed it would make them safer online. If they call with a problem, I need to be able to help, not just shrug my shoulders and tell them to call Apple.
Over the past few weeks, I have found Mac malware and Windows malware side by side on the exact same compromised web sites, served up by Google search results. The visuals and the payloads are tailored to match the visitor’s computing environment, but the social-engineering tricks are identical and are specifically designed to snare unwitting victims.
Apple, Google, and Microsoft should be working together to respond to this problem, but that doesn't appear to be happening.
So how effective has Apple's response been so far? Not very.
As I noted last week, Apple has begun playing a frustrating game of cat and mouse with the bad guys. They have released a new set of malware definitions for the XProtect feature in OS X 10.6.7 every day since they released Security Update 2011-003 last week. Six days, six updates so far. And each time the criminals behind the Mac Defender family have revised their product within a few hours so that it bypasses those signatures.
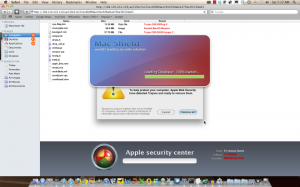
I captured two more samples of the latest Mac Defender variant in action on Saturday and Sunday. It’s now called Mac Shield:
Its behavior is essentially the same as before. It pops up fake warnings to scare the victim into paying to "register" the product. And if those warnings aren't effective, it begins opening pages from porn sites every few minutes. I confirmed over the weekend that this behavior still occurs even on a fully patched Mac with the latest XProtect malware detection signatures.
As Apple is learning, signature-based security software is ineffective against this type of attack. As soon as a new update comes out, the malware authors tweak their code and re-release it. The bad guys always have an advantage.
In addition, Apple's code has been giving some Mac users problems. Intego reports that the Security Preferences option isn't working for some users. There are also numerous reports on Apple's discussion groups of the malware removal tool causing problems with CPU usage:
since I installed the latest Apple security update on BOTH of my MacBook Pro and iMac (both running OS X 10.6.7), CPU utlization has been fluctuating with fan-on between 40% and 90% constantly - I have never seen this before. This type of 'upgrade' reminds me so much of the ill-fated Windows security releases and why I switched over to Mac in the first place! I hope this isn't typcial.
Not only that, but Apple has left a significant chunk of its user base out in the cold. According to Net Market Share stats, roughly 30% of all Mac users are using OS X versions 10.5 or 10.4; but Apple’s security update is only available for version 10.6.7.
Update: As a commenter reminds me, Apple has also not recommended changing the default Safari setting that makes this particular implementation so dangerous. As I wrote last week, the current attack "assumes that the user has visited the SEO-poisoned site using Safari (the default browser in OS X) and that the browser’s default settings are in use. You can block the automatic installation in Safari by clicking File, Preferences, and then clearing the Open “Safe” Files After Downloading check box." And yet Apple's security update 2011-003 does not mention this setting at all.
As a result, new victims are showing up on Apple’s support forums every day looking for help. In a cursory search yesterday, I found more than a dozen fresh reports of infections by the latest Mac Shield variant.
If you look on YouTube, you can find videos I’ve captured that show how these attacks work. The most common response I hear when people see them is: “You’d have to be a complete moron to fall for this.” Sadly, that’s not true. Computers are frightening to a lot of people who most assuredly are not stupid, and the bad guys are very good at creating fake error messages that look like the real thing.
These criminals prey on the weak, the feeble-minded, the ill-informed, and the technically unsophisticated. They are perfectly happy to play a numbers game that appears to be stacked against them.
For the sake of argument, let’s assume that only 1 in 100 people who own PCs or Macs even see one of these poisoned sites over the course of a month. That means 99% of us will never even encounter a fake AV program in the wild.
And then let’s assume that only 1 in 100 of that sliver of the worldwide computing population actually falls for the scam and gives up a credit card number. If you’re being barraged by warnings and porn sites popping up on their displays, and you don't have enough experience to find help, that's an understandable response.
Using that set of assumptions, 99.99% of PC and Mac users will be smart enough to avoid falling for the scam.
The trouble is, there are a billion PCs and nearly 50 million Macs in the world. Even that seemingly tiny success rate of 0.01%—1 in 10,000—means the bad guys will divvy up more than $5 million in revenue over the course of a month. And that doesn’t count whatever they’re able to pilfer if they steal and reuse the credit card numbers they harvest.
Computer crime is a problem that affects all of us, regardless of what platform we use. We are all being targeted by gangs that are depressingly effective. Apple, Google, and Microsoft should be working together to come up with a collective response. That doesn’t appear to be happening.
Related stories
- New Apple antivirus signatures bypassed within hours by malware authors [Update]
- Crying wolf? Apple support forums confirm malware explosion
- What a Mac malware attack looks like
- Why malware for Macs is on its way
- Malware authors target Google Chrome
- IE9 versus Chrome: which one blocks malware better?