Will your business be next? Customisable ransomware makes it easy for criminals to target organisations

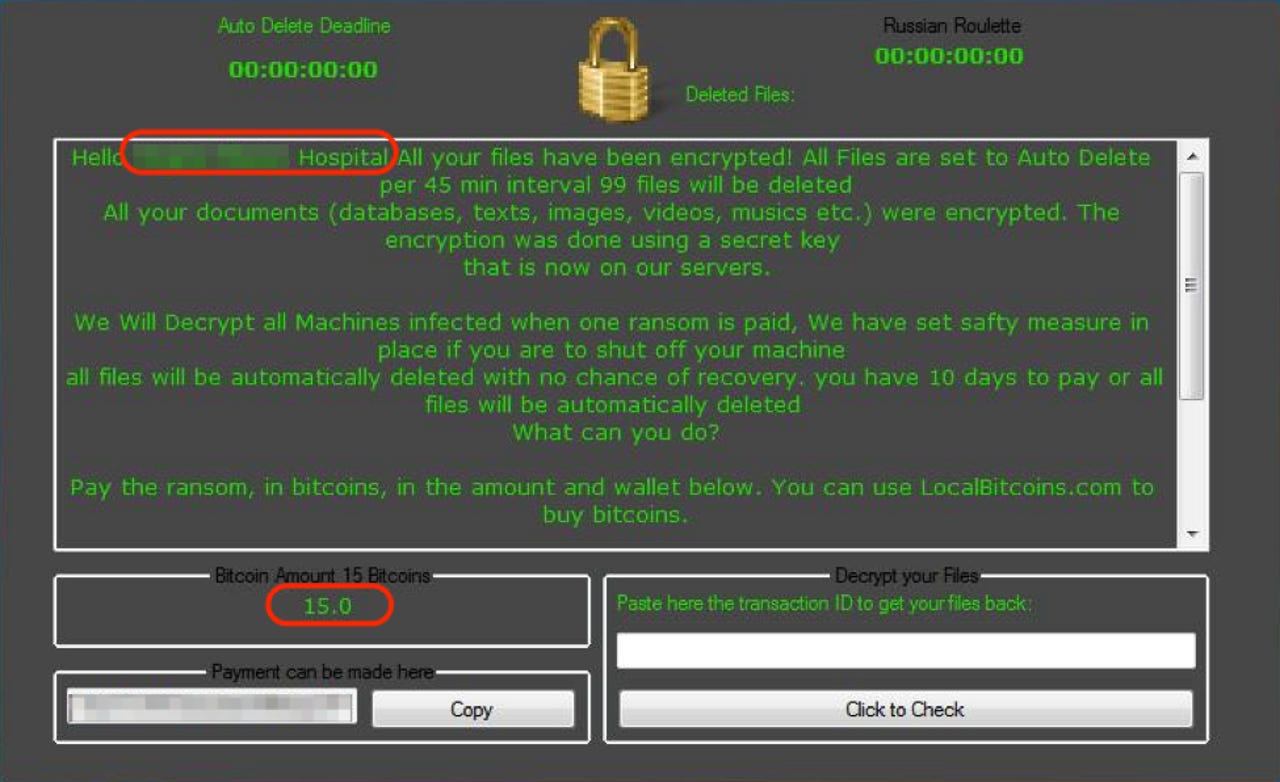
A custom ransom demand referencing the name of the target hospital.
An easy-to-use form of customisable ransomware is allowing entry-level cybercriminals to carry out targeted-ransomware campaigns.
First spotted in September last year, Philadelphia ransomware is not only simple to customise and deploy, but those using it also receive regular updates and support from its authors.
Ransomware has boomed over the past year, costing its victims some $1bn during 2016 alone.
But while most forms of ransomware are associated with large-scale "spray and pray" campaigns, in which criminals send out thousands, even millions, of emails in the hope of infecting random consumer and business targets, Philadelphia allows for the creation of highly targeted campaigns, which can even be focused around one organisation.
Cybersecurity researchers at Proofpoint have detailed a recent Philadelphia ransomware campaign that saw one threat actor use it to target specific healthcare institutions in a single city.
In this instance, attackers sent phishing emails appearing to be from an employee within the organisation, marked high importance and featuring subjects such as 'Patient referral'. The lure supposedly contained information about a patient behind a shortened link, which, if clicked, downloaded the ransomware.
Philadelphia ransomware lure claiming to contain urgent information about a hospital patient.
Those behind this attack have also customised the ransom note, not only referring to the hospital target by name, but also setting a high ransom demand of 15 Bitcoins (worth approximately $18,000) in the knowledge that networks are critical to hospital operations and that, as demonstrated by an incident last year, healthcare victims will give into these high demands in order to protect patients.
This Philadelphia attack has also been customised to add extra urgency, with a threat to delete 99 files every 45 minutes.
A custom ransom demand referencing the name of the target hospital.
Researchers note this is the first instance of ransom note customisation spotted in the wild, but by tracking other campaigns, other instances of Philadelphia ransom note customisation were found being deployed in a number of different scenarios.
For example, one customised ransom note was found to be targeting individuals, seemingly designed to shame them about viewing adult content and demanding a ransom of 0.05 Bitcoins, or about $49.
The ransom note also threatens to delete three files every hour before deleting all files after three days. Researchers have not yet determined how this version of Philadelphia spreads.
A custom version of Philadelphia ransomware designed to extort money from individuals by demanding lower ransoms.
Researchers also discovered Philadelphia targeting Russian language speakers, demanding a ransom of $200 and a no-nonsense approach to speaking to victims. "Do not write to us if you do not like the price. We do not bargain," reads part of the note after translation, which also includes a threat to raise the ransom demand the longer the victim takes to pay.
Russian Philadelphia ransom demand.
While Philadelphia isn't a particularly sophisticated form of ransomware, and doesn't have anywhere near the market proliferation of the likes of the notorious Cerber or Locky, researchers note that it represents a development in "commodity ransomware", allowing low-level cybercriminals to use highly customisable ransomware at a low cost.
Philadelphia is available to purchase for $400 in the underground markets, Patrick Wheeler, director of threat intelligence at Proofpoint, told ZDNet. He explained that those behind it offer advice and updates on the ransomware as if it was any other piece of business software.
"The authors created a YouTube video explaining the features and how to get in touch to obtain the malware, which includes a perpetual license and free updates," he said.
Meanwhile, for those who don't want to hand over money to other cybercriminals, there are cracked versions of the ransomware which can be downloaded for free.
The rise of this form of ransomware could become a big threat to organisations, warn Proofpoint, especially if criminals can successfully spoof emails to make them appear to be coming within the targeted organisation.
"As commodity ransomware becomes more sophisticated and customizable, new strains emerge rapidly, and ransomware-as-a-service becomes more commonplace, the possibilities for threat actors to use this type of malware in unexpected ways increase," say researchers.
However, the good news is that some strains of Philadelphia have been cracked and free decryption tools are available.
Ransomware has become one of the biggest menaces on the web. This ZDNet guide contains everything you need to know about it: how it started, why it's booming, how to protect against it, and what to do if your PC suffers an attack.
READ MORE ON CYBERCRIME
- Ransomware: How to defend yourself against it [CNET]
- How Bitcoin helped fuel an explosion in ransomware attacks
- Ransomware is now so awful it's actually making us take security seriously
- NHS trusts become top target for ransomware campaigns
- Ransomware attacks grew 600% in 2016, costing businesses $1B [TechRepublic]