Windows 7's default UAC bypassed by 8 out of 10 malware samples
A recently conducted test by malware researchers reveals that eight out of ten malware samples used in the test, successfully bypassed Windows 7's default UAC (user access control) settings. The findings were also confirmed by a separate test done by another company, with an emphasis on how one of the most popular scareware variants bypassed Windows 7's default UAC's settings as well.
More info:
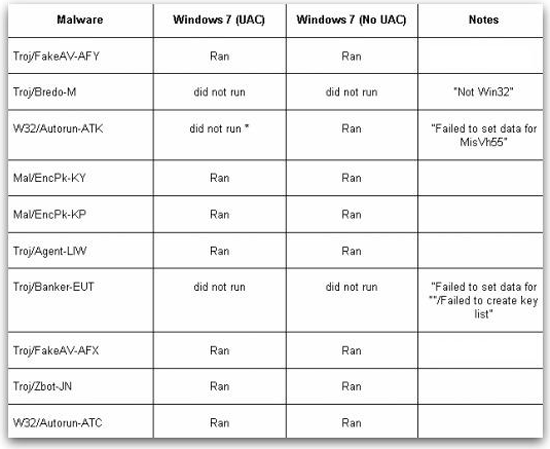
On October 22nd, we settled in at SophosLabs and loaded a full release copy of Windows 7 on a clean machine. We configured it to follow the system defaults for User Account Control (UAC) and did not load any anti-virus software.
We grabbed the next 10 unique samples that arrived in the SophosLabs feed to see how well the newer, more secure version of Windows and UAC held up. Unfortunately, despite Microsoft's claims, Windows 7 disappointed just like earlier versions of Windows. The good news is that, of the freshest 10 samples that arrived, 2 would not operate correctly under Windows 7.
Just like end users, enterprises already migrating to Windows 7 face the same security issues. Eric Voskuil, CTO, BeyondTrust -- the company that issued a report earlier this year, claiming that 92% of critical Microsoft vulnerabilities are mitigated by Least Privilege accounts -- believes that the required administrator privileges for using the feature may in fact pose new security challenges:
In response to feedback that users were forced to respond to too many prompts in Windows Vista, the new operating system introduces a new approach to User Account Control (UAC), providing a four-position “slider” feature to control how often UAC pop-ups occur. While these changes to Windows 7’s UAC benefit the home user market, enterprises must recognize that the new slider feature can only be applied to users logged in as administrators and may increase security risks.
Further, Windows 7 introduces no new features to solve the application compatibility issues experienced by standard users in previous versions of the operating system. “The most secure configuration option for enterprises that deploy Windows 7 remains running end-users as standard users, with administrator rights removed,” said Eric Voskuil, CTO, BeyondTrust.
What do you think about Windows 7's user access control slider? Is it a step in the right direction, or does it have the potential to provide a lot of users with a false feeling of security, making them believe that a stand-alone HIPS (host based intrusion prevention/behavior blocking) solution isn't necessary?
TalkBack.