Phishing-based breach of salesforce.com customer data is more evidence of industry's need to act on spam. Now.

Last night, in a notice urging vigilance and a series of best practices, salesforce.com sent an e-mail to its customers notifying them that a variety of recent phishing attacks -- both against salesforce.com employees as well as against salesforce.com customers -- were successful at compromising their targets. Although the connection isn't absolutely clear, it appears as though a phisher was successful at socially engineering a salesforce.com staffer into revealing personally identifying data about salesforce.com's customers which in turn may have led to phishing attempts on those customers, some of which were successful. Said the e-mail:
...we have seen a rise in phishing attempts directed at salesforce.com customers over the past few months.....When we first saw signs of this sudden rise, we conducted a thorough analysis. We learned that a salesforce.com employee had been the victim of a phishing scam that allowed a salesforce.com customer contact list to be copied. To be clear, a phisher tricked someone into disclosing a password, but this intrusion did not stem from a security flaw in our application or database. Information in the contact list included first and last names, company names, email addresses, telephone numbers of salesforce.com customers......
.....As a result of this, a small number of our customers began receiving bogus emails that looked like salesforce.com invoices, but were not—they were also phishes. Unfortunately, a very small number of our customers who were contacted had end users that revealed their passwords to the phisher....
The e-mail then goes on to mention that an additional perhaps more broadly reaching (in terms of salesforce.com customers) phishing attack had been detected -- one that includes malware (eg: keystroke loggers) designed to surreptitiously gather information such as user IDs and passwords from the victim's systems.
Whereas the initial "phish" of salesforce.com customers was apparently limited in scope to a small subset of salesforce.com's overall customer-base (tied to the list of customers whose data was socially engineered out of the aforementioned saleforce.com employee), this more recent wave targeting salesforce.com customers (the one that includes the malware payload) is probably more of a traditional phish whereby the phishers are blanketing their own database of targets hoping that some percentage of them are indeed salesforce.com customers, and hoping that some percentage of those take the bait.
The e-mail from salesforce.com notes how the on-demand CRM service provider is near its 1 million-subscriber mark -- a number that puts salesforce.com in rare company, but a number that also commands the attention of phishers whose likelihood of success is very much tied to the popularity of the companies they impersonate. The more popular the company they impersonate (ie: eBay, Bank of America, PayPal, etc.), the greater the likelihood that the inboxes they spam with their phishing attempts will belong to the customers of those businesses. That's why they call it phishing (the phisher's are fishing for customers).
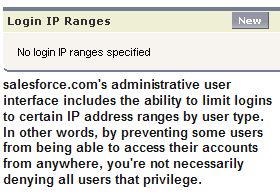
Modify your Salesforce implementation to activate IP range restrictions. This will allow users to access Salesforce only from your corporate network or VPN, thus providing a second factor of authentication.
The image (above left) shows the part of the salesforce.com user interface where administrators can whitelist the IP address ranges from which users can access their accounts. It's definitely a cool anti-phishing feature that more services should consider including as an optional administrative user element.
Beyond the list of recommendations and counter-measures salesforce.com recommends taking, the e-mail also says that saleforce's "recent and ongoing actions" in an effort to be proactive about customer security "include evaluating and developing new technologies both for our customers and for deployment within our infrastructure. We will regularly update you on these security innovations."
The email goes on to say:
Unfortunately, phishing is a reality on the Internet these days. But with the right mix of awareness, education, and preventive technology, the consequences of phishing don't have to be part of that reality.
Yes, phishing is unfortunate. But it doesn't have to be a part of the Internet's reality.
If salesforce.com is truly interested in a longer term solution, it will first realize that phishing is little more than a malicious form of spam that relies on all the same techniques that "regular"spam relies on to get opened by its targeted recipients. To the extent that phishing relies on these techniques, phishing relies on the same weaknesses in the Internet's e-mail system that spam relies on; for example lack of a standard way to authenticate senders. Or, lack of a standard protocol between e-mail clients and e-mail servers that gives clients a way to notify servers of the end-user's sender-whitelisting or sender-blacklisting preferences. Or, a standard protocol to handle the transmission of subscription and unsubscription information between end-users and services (today, the non-standard nature of unsubscription leaves too much of the reliability of the process to chance -- especially when active Internet connectivity is a prerequisite to success).
Another issue? Although they're physically possible with many e-mail systems, encryption and digital signing of e-mail -- two measures that can also play a role in eliminating spam (and phishing) -- need to be more seamlessly embedded into e-mail clients in such a way that they're easy to use. Today, the user experience varies widely from one e-mail solution to another and the phrase "ease of use" can hardly be associated with most deployments. This must change.
Once salesforce.com realizes that action must be taken in the area of industry consensus and standards around e-mail security, perhaps it can use its influence with the other large organizations who are in a position to make a real difference: Microsoft, AOL, Google, and Yahoo (the group I call "maggie"). Where consensus and ubiquity of some defacto standards are required (we can't wait for any of the standards bodies to get to this), those are truly the four companies (given the penetration of their e-mail solutions into the market) that together can bring about change. So far, the four companies have yet to band together once and for all to put an end to the scourge that plagues all of us, and now, salesforce.com too. Perhaps now that spam has bubbled onto salesforce.com's radar to the point that it's posing a serious threat to the company's customers, the next thing salesforce.com can do is work on pulling the industry together around this problem. Especially since no one else will.