Anatomy of a malware attack: the complete Mac Defender timeline

Over the past two months, I have written extensively about the sustained malware attack that OS X users had to deal with throughout the month of May, until the criminal gang behind it suddenly shut down on June 23.
Update: One possible explanation for the sudden shutdown? The head of the gang that processed payments for the rogue outfit was arrested on June 23.
Anyone who tries to argue that this was no big deal has simply not been paying attention. It was enough to thoroughly disrupt Apple's normally smooth-running support operation, and Apple responded in unprecedented fashion by publicly adding significant new malware detection and removal features in an update to Snow Leopard that was also incorporated into the new Lion update. Making that sort of system-level change is neither easy nor cheap.
This is a confusing story, one that evolved significantly over time. If you're trying to make sense of it all, this timeline should help. It includes a link to each post I published on the subject, with the date/time stamp and an excerpt. (I've also included a link to one excellent third-party post.)
Just scanning this chronology should give you a better understanding of how this attack evolved. Click any link to dig a little deeper.
Coming soon to a Mac near you: serious malware
May 2, 2011, 9:42am PDT[N]ow that Macs have achieved a critical mass of success in the marketplace, they’ve attracted the attention of malware authors. According to a report from a Danish IT security company, an underground group has completed work on a fully operational kit specifically designed to build malware aimed at the Mac OS platform.
Why malware for Macs is on its way
May 5, 2011, 12:02pm PDTThe guys who run these operations are not master hackers—they are thugs who use point-and-click malware construction kits that they buy from rogue programmers. It’s a thriving business. And so far that software category, like so many legitimate software businesses, has been built on Windows. Its overwhelming market share meant that’s where the money was.
[…]
A gain of a few percentage points in the Mac market might not seem like a lot, but in a universe with a billion Internet-connected devices, each percentage point equals a potential 10 million victims. A market with 60 million, 80 million, or even a hundred million Mac users is big enough for the bad guys.
[…]
My prediction is that the bad guys are still “testing market conditions,” and waiting for the right time for their grand opening. I think we’ll see a few more of these tentative probes—beta tests, if you will—before anyone unleashes a truly widespread attack. The trouble is, in this market, Mac users aren’t the customers—they’re the product.
Photo gallery: Mac malware in the wild
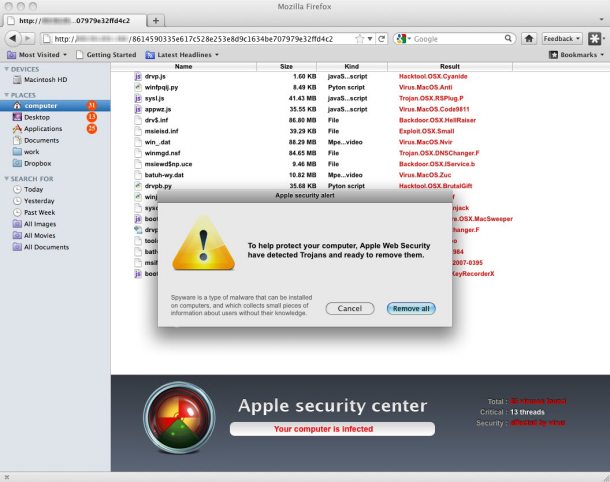
May 6, 2011 12:39pm PDTWhat a Mac malware attack looks like
May 6, 2011, 1:09pm PDTIt is easy to dismiss this as a crude attempt, and indeed, I don’t think many people are likely to fall for this attack. But dismissing this sample because it’s not particularly well done is like dismissing an entire computing platform because of a single poorly written app.
[…]
And note that the bad guys get better over time. This attack might be crude, but that doesn’t mean the next one will be. I have seen some remarkably effective phishing attempts. In the hands of a skilled gang of thieves, this approach could cull out the weaker members of the Mac herd and create some genuine headaches for the friends or co-workers who have to provide emergency technical support.
An AppleCare support rep talks: Mac malware is "getting worse"
May 18, 2011, 5:21am PDTOver the weekend, I got an e-mail from an AppleCare support rep, who was responding to my recent reports of Mac malware being found in the wild. At least one prominent voice in the Mac community dismisses these reports as “crying wolf.” The view from inside an Apple call center says it’s for real: “I can tell you for a fact, many, many people are falling for this attack.”
A May 19 post by Jacqui Cheng at Ars Technica, Malware on the Mac: is there cause for concern? confirms many details of the scale of this problem:
A support specialist who we'll call Carl works at an Apple Authorized Campus Store and threw in his two cents as well. "I have never had to remove a virus or malware from a Mac until this month," Carl told Ars. "Now we have had a handful of people come in with MAC Defender on their computer."
[...]
It gets worse as the stores scale up. We spoke to another Apple Store Genius, who we'll refer to as Andy, whose store services a couple thousand Macs per week. "There's been a very real uptick in the number of malware instances we've seen," Andy, said, adding that in the past, 0.2 percent of the Macs brought into Andy's store might have a malware problem—"most always DNS trojans."
That has changed in the last three weeks. Nowadays, something like 5.8 percent of machines Andy's store sees have a malware-related issue, almost entirely made up of MAC Defender or some variant.
Crying wolf? Apple support forums confirm malware explosion
May 18, 2011, 11:00am PDTYesterday I spent several hours going through discussions.apple.com and collecting requests for help from Mac users who have been affected by this issue. I found more than 200 separate discussion threads, many of them from people who have been tricked into installing this software and are desperately trying to remove it. It started with four posts on April 30; this past weekend there were 42 unique, new discussion threads on this subject.
I am not unfamiliar with Apple’s forums. I’ve done similar searches in the past, especially after reading some of those same posts that Gruber called out from 2008. I have never found more than one or two in-the-wild reports. This time, the volume is truly exceptional.
Apple to support reps: "Do not attempt to remove malware"
May 19, 2011, 5:00am PDTApple is actively conducting an internal investigation into the Mac Defender malware attack I wrote about yesterday ... An internal document with a Last Modified date of Monday, May 16, 2011 notes that this is an “Issue/Investigation In Progress.”
The document (shown below) provides specific instructions for support personnel to follow when dealing with a customer who has called AppleCare to request help with this specific attack.
[…]
- Do not confirm or deny that any such software has been installed.
- Do not attempt to remove or uninstall any malware software.
- Do not send any escalations or contact Tier 2 for support about removing the software, or provide impact data.
- Do not refer customers to the Apple Retail Store. The ARS does not provide any additional support for malware.
This is a continuation of the Mac Defender timeline, as documented in real time at this blog.
Apple continues to tell support reps: do not help with Mac malware
May 23, 2011, 11:49pm PDTSo how big is the problem? Apple’s silence makes it impossible to know for sure. However, I’m told that the division that handles Mac support calls receives between 10,000 and 20,000 calls a day. If 25% of those calls are related to this issue, which has been going on for 25 days, the total number of customers affected could be between 60,000 and 125,000, and growing.
Update May 24, 4:30PM PDT: Apple has now posted a support article on its website: How to avoid or remove Mac Defender malware. A note at the top of the article says:
In the coming days, Apple will deliver a Mac OS X software update that will automatically find and remove Mac Defender malware and its known variants. The update will also help protect users by providing an explicit warning if they download this malware.
Mac malware authors release a new, more dangerous version
May 25, 2011, 12:05pm PDTWithin 12 hours of Apple’s announcement, the author of the original Mac Defender program had a new variant available that renders key portions of the current Mac Defender prevention plan obsolete.
[…]
The new architecture seems to be a specific response to Apple’s instructions in the Mac Defender security note: “In some cases, your browser may automatically download and launch the installer for this malicious software. If this happens, cancel the installation process; do not enter your administrator password.”
In this new variation, no password is required as long as you’re logged in using an administrator account. That might lull a potential victim into thinking they’re safe.
New Apple antivirus signatures bypassed within hours by malware authors
May 31, 2011, 1:59pm PDTAfter a month-long Mac Defender/Mac Guard malware attack, Apple has finally released the security update it promised last week. The update takes Apple one step closer to turning an obscure security feature into something very close to full-fledged antivirus software.
Security Update 2011-003 includes changes to the File Quarantine feature, which beginning with Snow Leopard also includes antimalware checks for files downloaded through web browsers, e-mail, and other common paths. This update includes definitions for Mac Defender and its known variants, as well as an automated removal tool. It works only with the most recent version of Snow Leopard, 10.6.7. Earlier versions of OS X are apparently not included.
[...]
Here's a start-to-finish, unedited "before" video that shows how the Mac Guard fake AV program goes from a seemingly innocent Google search result to a full install in just three clicks, with no password required. This demo uses the latest version of OS X 10.6 and the default browser, Safari, with its default settings.
Why Windows users should care about malware on Macs
June 6, 2011, 5:17am PDTAs I noted last week, Apple has begun playing a frustrating game of cat and mouse with the bad guys. They have released a new set of malware definitions for the XProtect feature in OS X 10.6.7 every day since they released Security Update 2011-003 last week. Six days, six updates so far. And each time the criminals behind the Mac Defender family have revised their product within a few hours so that it bypasses those signatures.
[…]
As a result, new victims are showing up on Apple’s support forums every day looking for help. In a cursory search yesterday, I found more than a dozen fresh reports of infections by the latest Mac Shield variant.
[…]
The trouble is, there are a billion PCs and nearly 50 million Macs in the world. Even that seemingly tiny success rate of 0.01%—1 in 10,000—means the bad guys will divvy up more than $5 million in revenue over the course of a month. And that doesn’t count whatever they’re able to pilfer if they steal and reuse the credit card numbers they harvest.
Has Apple done enough to fight malware on Macs?
June 19, 2011, 4:36pm PDTThe anti-malware feature in Security Update 2011-003 is clearly a stopgap solution designed to disrupt a single threat—Mac Defender. Until Apple addresses the glaring insecurity in Safari, it’s hard to take their response seriously.
I still believe the Mac Defender attack was a successful proof of concept for the bad guys. The social engineering was excellent, and I am certain it brought in enough ill-gotten gains to bankroll the next phase of development.
Remember, this was done via a malware toolkit—the first one ever released for the Mac platform. The next version of this toolkit is being written with full knowledge of how Security Update 2011-003 works. The bad guys are counting on Apple taking weeks to work up its response. That could make Mac Defender version 2.0 very nasty indeed.
Where did all the Mac malware go?
August 1, 2011, 3:00am PDTBased on my observations, I think this malware campaign simply ran its course. Apple’s response made a small dent in its impact. More importantly, Google got much better at detecting the poisoned search results and blocking them, which lowered the rate of return on Mac Defender installation attempts. In my June 19 analysis of Apple’s response, I referred to the attack in the past tense and speculated that it was about to end.
[…]
And indeed, there is now some sketchy evidence to suggest what the next wave of Mac malware will look like.
On June 16, someone uploaded a compressed file to VirusTotal.com for analysis. It was detected by 4 of 42 antivirus engines as a generic Windows Trojan that steals passwords and performs keystroke logging. But the interesting detail didn’t emerge until a few weeks later, when security researchers at the Microsoft Malware Protection Center (MMPC) took a closer look at the file and determined that it actually included two packages—one for Windows, and one for OS X.