Bing ads lead to more malware; new Mac Trojan in the wild

Yesterday, I showed you details of an ad on Microsoft’s Bing search engine that led unwary visitors to a site serving up malware.
Several hours after I reported that ad to Microsoft, it was removed, and a spokesperson told me that Bing’s ad network will “continue to directly work with our agency media partners to verify and confirm any suspicious orders.”
Looks like there’s more work to do.
This morning, I’ve found multiple ads on Bing that go through seemingly innocent intermediary sites to the same malicious server in Russia.
Here, for example, is a pair of ads that appeared at the top of the Bing search results for firefox download:
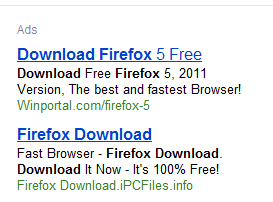
Clicking the second ad in that block leads to a site called ipcfiles.info. The landing page is just as convincing as the fake Google Chrome downloads I identified yesterday:
Likewise, a Bing search for flash player displays this block of ads above the search results.
Clicking the second ad in this group, which is served from a site called oeachot.info, leads to this landing page:
Again, this is convincing social engineering.
Both intermediary sites use scripts that redirect an unwary user to the same Russian server I flagged yesterday.
I found similar ads, all leading to the same server, when I searched Bing for adobe reader, utorrent, and google earth.
This sort of attack has a higher than average probability of success, because casual Internet users have become accustomed to using search engines as a jumping-off point, and both Bing and Google place ads in prominent positions above search results, where they’re more likely to be clicked.
And because this gang uses a polymorphic engine, the files it delivers are not detected by conventional antivirus scanners. When I submitted both of these samples to VirusTotal today, only 3 of 43 scanning engines detected them as suspicious.
Currently, these ads lead only to Windows malware, but it’s possible that Mac users will be targeted by similar types of attacks. Last week, F-Secure identified a fake Flash Player installer delivered as a Mac package that is actually a DNS-changing Trojan.
Over the weekend, a customer on Apple’s support forums reported finding this on his Mac, and this morning I confirmed that Apple has updated its XProtect signatures to include a definition that flags and removes this threat, which it calls OSX.QHost.WB.A. This is the first definition update for OS X since the takedown of the Mac Defender gang on June 23.
Related posts: