Malware authors target Google Chrome

Every time I write about Internet Explorer, it's usually a matter of minutes—sometimes even seconds—until someone in the Talkback section proclaims, smugly, that they’ve switched to Google Chrome or Firefox and are therefore immune from malware attacks.
They’re wrong, and malware authors have begun preying on users of alternative browsers to push dangerous software, including Trojans and scareware. The problem is that most malware attacks aren’t triggered by exploits that target vulnerabilities in code. Instead, according to one recent study, “users are four times more likely to come into contact with social engineering tactics as opposed to a site serving up an exploit.”
Follow-up: Malware attempts that use Apple-focused social engineering are now in the wild. I just found one via Google Image search. See for yourself: What a Mac malware attack looks like.
I found a perfect example yesterday, thanks to an alert from Silverlight developer Kevin Dente. He had typed in a simple set of search terms—Silverlight datagrid reorder columns—at Google.com, using the Google Chrome browser on Windows. You can follow along with what happened next in the screenshot gallery that accompanies this post.
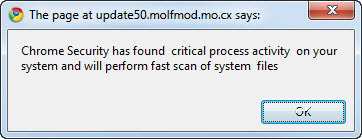
The first page of Google search results included several perfectly good links, but the sixth result was booby trapped. Clicking that link in Google Chrome popped up this dialog box:
That led to a basic social engineering attack, but this one has a twist. It was customized for Chrome. If you’ve ever seen a Google Chrome security warning, you’ll recognize the distinctive, blood-red background, which this malware author has duplicated very effectively.
After the fake scan is complete, another dialog box comes up, warning that "Google Chrome recommends you to install proper software."
That’s terrible grammar, and this social-engineering attack is likely to fail with an English-speaking victim, who should be suspicious of the odd wording. But a user whose primary language is something other than English might well be fooled. And the malware author has anticipated the possibility that you might click Cancel in the dialog box. If you do, it still tries to download the malicious software.
Each time I visited this page, the download I was offered was slightly different. My installed antivirus software (Microsoft Security Essentials) didn’t flag it as dangerous. When I submitted it to VirusTotal.com, only five of the 42 engines correctly identified it as a suspicious file. Less than 8 hours later, a second scan at VirusTotal was a little better. This time, eight engines confirmed that the file was suspicious. Microsoft’s virus definitions had been updated and a scan identified the rogue file as Win32/Defmid.
Panda and Prevx identified the file as "Suspicious" and "Medium risk malware," respectively. BitDefender, F-Secure, and GData flagged it as "Gen:Trojan.Heur.FU.quX@am@e97ci." AntiVir detected it as "TR/Crypt.XPACK.Gen." Kaspersky says it is "Trojan-Downloader.Win32.FraudLoad.zdul." Every other antivirus engine, as of a few minutes ago, waved this suspicious executable right through.
Meanwhile, back in the browser, Google Chrome’s warnings are completely generic. If you download the software it shows up in the Downloads folder looking perfectly innocent.
Interestingly, this set of “poisoned” search terms also affected Bing, although the dangerous search result was on a different site, which didn’t show up until the fifth page of search results. And the download that it offered was, apparently, a completely different Trojan/scareware product. But the end result would have been the same, regardless of which browser I was using.
This case study shows that malware authors are beginning to adapt to changing habits of PC users. There’s nothing inherently safer about alternative browsers—or even alternative operating systems, for that matter—and as users adapt, so do the bad guys.
Be careful out there.