New wave of phishing attacks serves malware to PCs and Macs

In the past few weeks, I’ve noticed an alarming increase in fraudulent email messages coming to some old, well-established email addresses of mine.
It’s not just the quantity of messages that’s noteworthy, it’s the quality as well. This particular wave of attacks includes some attacks that are frighteningly real looking. And they’re being used to serve up a toxic brew of malware to unprotected systems.
Consider these two examples of messages I received this week. The first appears to be a fraud alert from American Express:
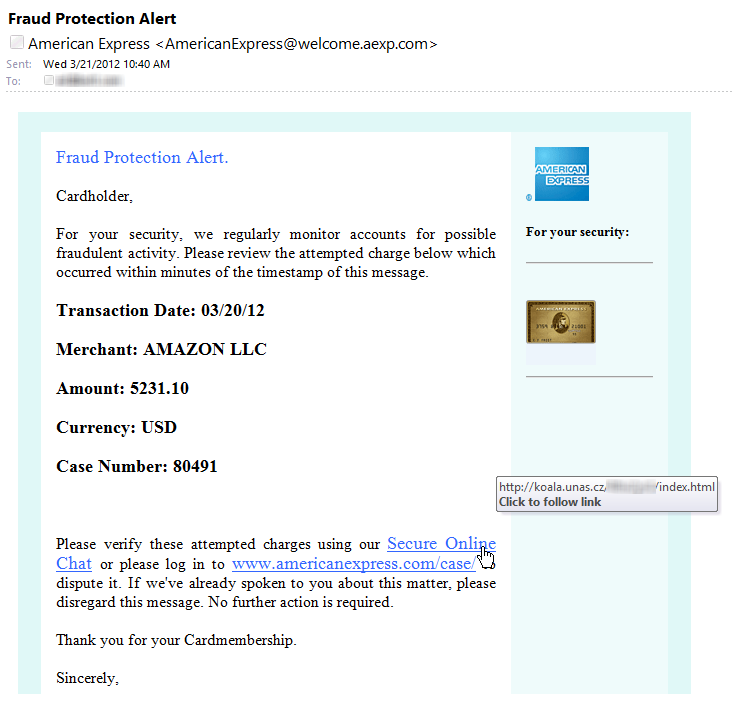
It has all the right logos, and the wording has the same professional tone and grammatical accuracy I would expect of a legitimate communication from American Express. Unlike many phishing messages, this one made me look much more closely, and I suspect that the click-through rate was higher than most such attempts.
Related:
- If your PC picks up a virus, whose fault is it?
- Why do people fall for Trojans?
- Trojans, viruses, worms: How does malware get on PCs and Macs?
- Stay safe online: 5 secrets every PC (and Mac) owner should know
- Do you really need antivirus software?
In the screenshot above, I’ve rested the mouse pointer over one of the links in the message. It doesn’t lead to an official AmEx site, but rather to a compromised site hosted at a domain in the Czech Republic.
Even more interesting is the destination. Historically, phishing attacks try to re-create a legitimate site, with the goal of convincing the victim to enter his or her username and password. Clicking this link led to a site that served up a variant of the Blacole (aka “blackhole”) exploit capable of installing a very nasty data-stealing Trojan on a PC or Mac that’s running outdated versions of Java, Adobe Shockwave, Adobe Acrobat and Reader, and other third-party software.
The target sites are probably running outdated WordPress installations that were remotely compromised to serve up a collection of exploits aimed at unpatched systems.
Another wave of messages to this account appeared to be from LinkedIn (ZDNet’s Dancho Danchev also flagged this attack earlier in the week). Again, they were skillfully done. Even a cautious recipient could be convinced to click one of the target links.
This sample led to another compromised website serving up a similar collection of exploits from the Blacole family.
Update: Danchev has more details on the LinkedIn wave of attacks in this post at the Webroot Threat Blog:
The campaign is using real names of LinkedIn users in an attempt to increase the authenticity of the spamvertised campaign.
The cybercriminals behind the campaign are currently relying on thousands of compromised legitimate sites, in an attempt to trick Web reputation filters into thinking that the payload is not malicious. Combined with the ever-decreasing price for launching a spam campaign through a botnet, the cybercriminals behind the campaign will definitely break-even from their original investment, and achieve a positive ROI (return on investment).
Mac users aren't immune from this type of attack either. In recent weeks, security researchers I stay in touch with have observed an uptick in installations of the OSX/Flashback Trojan, which can be installed automatically via Java exploits or interactively, via social engineering.
The best protection available for this type of attack isn’t antivirus software; it’s a good spam filter and an effective update routine. Most of these messages were correctly flagged as spam by Microsoft Outlook, which moved them to the Junk E-mail folder and disabled all links. It also converted the HTML to plain text, making the fraudulent links obvious.
That combination of measures effectively kneecapped the potential exploit. To trigger the infection, the recipient would have to move the message to the inbox and then click on the booby-trapped link.
Even if a user could be convinced to click on the links, the exploits in question won't work on a system that is properly updated. The exploits used in the two attacks I saw were aimed at vulnerabilities that were found and patched in 2010. Sadly, the population of computer users who ignore third-party software updates is big enough for this type of attack to be successful.