Windows Activation Technologies: an unauthorized inside look

Trust, but verify. That was good advice for dealing with the Soviet Union in its heyday, and it's equally sound policy today when dealing with that other Evil Empire. You know, the one in Redmond?
Last month, Microsoft rolled out an update to its Windows Activation Technologies (WAT) platform in Windows 7. Everything you've read about KB971033 so far, including my report last week, has been based on what Microsoft said it was going to do; in my earlier coverage, I gathered information from blog posts, published privacy policies, a Knowledge Base article, and some one-on-one interviews. But can you really believe everything Microsoft tells you about its new Windows Activation Technologies update?
Now that the update has been publicly available for a few weeks, I've been able to dig into it and determine exactly what it does. You don't have to take my word for it, either. You can download the same tools I used and check for yourself. (And don't miss my post from yesterday, Confessions of a Windows 7 pirate, which takes a similarly detailed look at the pirates' toolkit for cracking Windows activation.)
I tested on multiple PCs, running both x86 and x64 editions of Windows 7. To observe its activity, I collected traces using two tools:
- Process Monitor is the flagship utility from Sysinternals.com, originally developed by Mark Russinovich and Bryce Cogswell. (The company was purchased in 2006 by Microsoft. The Sysinternals utilities are currently hosted on Microsoft-run servers but are still maintained and regularly updated by Russinovich and Cogswell, both of whom are now Microsoft employees. ) I used the most recent release of Process Monitor, v2.8, to save a trace of all file, registry, and process activity associated with the installation and operation of the WAT Update.
- Wireshark is a free, open-source network protocol analyzer. I used version 1.2.6 with WinPcap version 4.1.1 to capture all network traffic while the WAT Update was running.
I installed the KB971033 update on multiple systems using both the downloaded version and the one delivered through Windows Update. I also uninstalled the update and observed what happened.
From a technical standpoint, I was able to confirm that the WAT update does what Microsoft says it does. I was not able to read the contents of the signed, encrypted packets going across the wire, but I did locate the stored information in the registry and compared it to Microsoft's published privacy policy.
You can see the full results of my tests on the next three pages. As I said, you don't have to take my word for it. I encourage you to do this for yourself so you can make your own decision based on your own evidence. If you see something different, let me know in the Talkbacks.
Page 2: What files does it install? What else does it do to your system? I was able to observe exactly which files it installed, and I also recorded changes it made to the registry and in Task Scheduler.
Page 3: What does the Windows Activation tool do when it runs? How does it communicate with Microsoft? I used details from the Process Monitor trace to identify which system licensing files are being checked, and I also confirmed that all communications with Microsoft servers were over secure connections.
Page 4: What information does it exchange? What happens when you uninstall it? I examined the privacy policy for the information exchange (and also verified a crucial certification for it). I also confirmed Microsoft's claim that the update can be uninstalled.
For details about what the installer does to your system, see the next page.
Page 2: What 's changed on your system? -->
<-- Previous page
What files does it install?
The KB970133 update creates a new folder called WAT under the Windows\System32 folder. It saves four files in this location.The four files are all labeled with version 7.1.7600.16395:
- WatAdminSvc.exe - Windows Activation Technologies Service
- npWatWeb.dll - Windows Activation Technologies Plugin for Mozilla
- WatWeb.dll - Windows Activation Technologies ActiveX Control
- WatUX.exe - Windows Activation Technologies UX
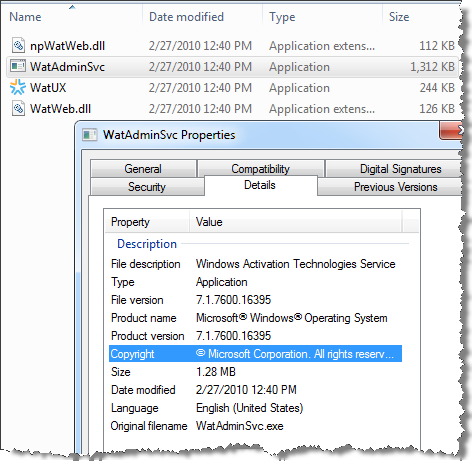
The installer also adds a digitally signed catalog file to the system and makes some log entries to record its activities.
What else does it do to your system?
On the systems I tested, the KB971033 update adds a new Windows Activation Technologies key and several subkeys to the registry. It uses this location to store result codes and two hashed identifiers, MachineID and GGUID.The installer also creates a new Windows Activation Technologies folder in Task Scheduler and adds two new entries to it. The first task is configured to run at the next restart and then to reset the task trigger so that it runs again 90 days later. The second task is configured to run a week after the first one. When the first task ran successfully on my test systems, the Next Run Time was set to a date 90 days in the future for the first task, and one week after that new date for the second task. (According to Microsoft, the purpose of the second task is to allow the update to run weekly after it detects and repairs a system whose activation files have been tampered with.)
Although the Windows Activation Technologies Service is installed and configured to run using the Local System account, its startup type is set to Manual. In my tests, it ran only when specifically called upon and exited when it had completed its work.
So what does the Windows Activation tool do when it runs?
Page 3: A close-up look at the WAT tool in action -->
<-- Previous page
What does the Windows Activation Tool do when it runs?
According to Microsoft, the WAT utility (which runs as a service using the Local System account) first checks the integrity of licensing files to ensure that they haven't been tampered with. In my Process Monitor trace, I saw what appeared to be multiple operations where the tool checked the properties of certain files against their signatures in the Windows digital signature catalog folders (catroot and catroot2).In my testing, the following file names appear on this list of files, along with multi-language user interface files associated with each. The SL prefix indicates code that is part of the Software Licensing subsystem; SPP indicates the Software Protection Platform.
- sppobjs.dll
- sppc.dll
- sppcext.dll
- sppwinob.dll
- slc.dll
- slcext.dll
- sppuinotify.dll
- slui.exe
- sppcomapi.dll
- sppcommdlg.dll
- sppsvc.exe
- spsys.sys
- spldr.sys
If any of these files are missing or tampered with, the system attempts to repair them. I did not see this repair behavior in operation on systems that were properly activated. When I forced the WAT Update to run on a system whose activation files had been tampered with using the latest RemoveWAT (v2.2.5), the utility was able to detect the tampering and flagged the system as non-Genuine. When I followed the online instructions and downloaded the components to try to repair the licensing subsystem, the download and installation appeared successful, but the activation components did not work. I had to use the Restore WAT button from the RemoveWAT tool to fix things properly.
Finally, the tool contacts a secure web site and runs a web service, where it downloads a list of signatures to identify known activation exploits. I was able to observe in the Process Monitor trace that the web service created a file in a secure Temp folder (presumably the template file containing exploit signatures) and then checked for the existence of a number of specific files. I saw checks that appeared to be aimed at specific activation exploits I've seen in my research, including those that create modified boot loaders and those that remove the WAT files.
How does the WAT update communicate with Microsoft?
Microsoft says its Web service runs over Secure HTTP. In my case, the web service made secure (HTTPS) connections with na.activation.sls.microsoft.com and with a web service (sl_wga.asmx) at validation.sls.microsoft.com. According to Microsoft, these connections download the latest template files containing signatures for known activation exploits and upload anonymized information used for aggregate reporting and analysis.In my case, the entire transaction was completed in just under 13 seconds.
How often does it run?
According to the initial settings of the main Scheduled Task created during installation of KB971033, it is set to run at the next startup. After it runs successfully, it sets its Next Run Time to 90 days later.Interestingly, I was able to adjust the settings of this utility so that it was set to run every 365 days, with the next run time set for one full year away. When I tried to set it for higher values (999 days and 730 days, or two years), the Task Scheduler refused to save my settings and gave me an error message instead.
Page 4: Privacy risks and uninstall details -->
<-- Previous page
What information does it exchange?
Because the connections are secure and therefore encrypted, it's impossible to see exactly what was in the packets that were exchanged. But it appears reasonable to assume that the uploaded information includes what is stored in the Windows Activation Technologies\AdminObject\Store key in the registry.According to Microsoft's privacy policy, no personally identifiable information is exchanged and the IP address of the uploading machine is not associated with the validation upload and is discarded within 24 hours after validation completes. Microsoft's privacy policy, which was last updated in February 2010, specifically lists the following items of information that are collected as part of the validation activity and may be included in the ID hashes shown in the screenshot above:
- Computer make and model
- Version information for the operating system and software
- Region and language settings
- A unique number assigned to your computer by the tools (Globally Unique Identifier or GUID)
- Product Key (hashed) and Product ID
- BIOS name, revision number, and revision date
- Hard drive volume serial number (hashed)
- Whether the installation was successful if one was performed
- The result of the validation check, including error codes and information about any activation exploits and any related malicious or unauthorized software found or disabled
If the validation check identifies an activation exploit, the following additional information is collected and will be transmitted to Microsoft's servers
- The activation exploit’s identifier
- The activation exploit's current state, such as cleaned or quarantined
- Original equipment manufacturer identification
- The activation exploit’s file name and hash of the file, as well as a hash of related software components that may indicate the presence of an activation exploit
- The name and a hash of the contents of the computer's start-up instructions file (commonly called the boot file) to help [Microsoft] discover activation exploits that modify this file.
The Windows Vista Software Protection Platform received the European Privacy Seal from EuroPriSe in November 2008. EuroPriSe is an independent consortium funded by the European Commission in 2007 and now led by the Independent Centre for Privacy Protection Schleswig-Holstein (Unabhängiges Landeszentrum für Datenschutz, ULD). A Microsoft spokesperson tells me a similar privacy certification process for the Windows 7 Activation Technologies began last summer and should be complete "within the next few weeks."
Update: Thanks to a commenter for providing this interesting recent overview of the EuroPriSe certification.