DDoS attack on UltraDNS affects Amazon.com, SalesForce.com, Petco.com

Several NeuStar UltraDNS managed DNS service customers, including Amazon.com, SalesForce.com, advertising.com and Petco.com, were knocked offline for several hours yesterday morning by a distributed denial of service attack, reports rival Dynamic Network Services.
Neustar confirmed the attack to NetworkWorld with the following statement:
"Early this morning, our monitoring systems detected a significant denial of service attack, which affected a small subset of our customers, in some cases for as long as a few hours. While we continue to investigate the cause, the extent, and the duration of the attack, service was completely restored by 10 a.m. EST."
Dynamic Network Services blogged about the UltraDNS outage first:
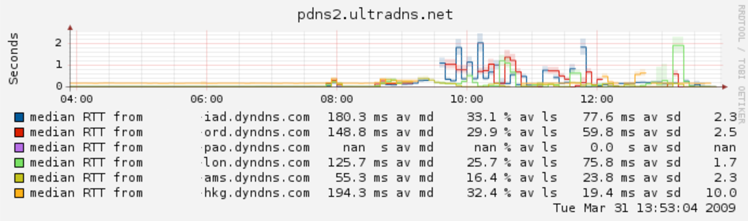
This morning, our Dynect Platform monitoring system noticed a problem, a big one. From our global perspective, it appears that many online services, including amazon.com (the store, AWS, and S3), salesforce.com, advertisting.com, and petco.com, had some serious DNS troubles. As many of our readers know, DNS is the glue that binds domain names, like dynect.com to their respective server’s IP addresses (204.13.248.122). Without DNS, nothing works; no web, e-mail, voip, IM, file sharing, etc.
The Dynect Team quickly began to analyze the situation by checking the resolution chains for these popular web sites. Our analysis revealed that multiple UltraDNS PDNS (a special class of ultradns server) nodes were failing to respond to all DNS queries. Amazon.com clearly knew about the problem, as our monitoring then detected a change in the delegation for amazon.com from UltraDNS’ PDNS nodes to their UDNS nodes at approximately 8:50 am Eastern.
According to NetworkWorld, Hitchcock said his company's Dynect Platform monitoring system saw heavy packet loss on UltraDNS name servers, with as much as 50 to 70 percent of responses being dropped.
Based in Reston, Va., NeuStar is a major provider of high-availability DNS services to e-retailers as well as high-tech companies such as Oracle and Juniper. NeuStar is also the registry for the .biz and .us domains, and provides telephone number look-up services for carriers in North America.