Have you received any "traceable" PattyMail recently?

The plan was to send Kawamoto a phony tip regarding an as-of-yet unannounced HP product in hopes that she'd pass it on to her insider at HP for verification. If the investigators could successfully trace the email as it was opened by Kawamoto and then forwarded to her source, then HP could have caught the insider red handed. This was one aspect of the investigation that HP CEO Mark Hurd was closely in touch with. He approved the falsified product information that was included in the e-mail.
The idea that HP or any company for that matter is capable of tracing e-mails as they get passed around the Internet is scary to some. But the truth of the matter is that it's done every day in the course of normal business practice. In fact, during his press conference on the matter last week, Hurd justified HP's usage of the technique on those very grounds -- that other businesses are engaged in the practice as well. But the fact that businesses (including CNet) can and are legally tracking what happens to the e-mails they send did nothing to assuage those whose alarms start ringing when they hear about such big brother techniques.
The HP incident raises two questions. The first of these is, of course, how and why are some of the e-mails sent to you being traced? I have the answer to that. Second, can you do anything to stop it? The answer? If you're an Outlook 2003 user there's actually a small Catch-22 in the way the software works that could force many users to allow such tracing where they might otherwise have disabled it.
There are a variety of ways to format the contents of an e-mail. Some e-mails are sent throught Internet with nothing but text. Others are richer in their presentation, often including embedded graphical elements. It's this second class of e-mails that's particularly susceptible to being traced. In many cases, such e-mails are HTML-based. HTML is the markup language of Web pages and when you attempt to open an HTML-based e-mail that has arrived in your inbox, your e-mail client will attempt to present that e-mail to you in the same way a Web browser would show you the same content. In the case of most HTML-emails, when an e-mail relies on an image, that image is not attached to the e-mail. Instead, the HTML in the e-mail tells your e-mail client to retrieve that image from a Web server that's out on the Internet. As is the case with any Web server, once you estabish a connection to a server in order to retrieve that image, that server can figure certain things out about you. For example, your IP address.
Such tracing is used for both legitimate and illegitimate reasons. For example, here at ZDNet, if you're subscribed to one of our HTML-based e-mail newsletters, we can tell when you open them and from where. There's no nefarious intent behind the "tracing" we do (if you can call it that). If today's newsletter only gets opened by 20 percent of the recipients but tomorrow's gets opened by 80 percent of the recipients, then we can improve the utility of our newsletters by trying to figure out what it was about today's newsletter that caused it to perform so bad? Was it a holiday? Was it a boring subject? You get the picture.
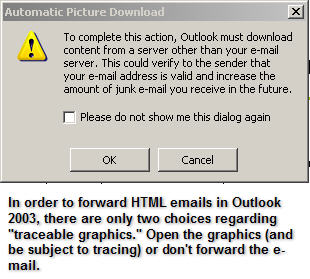
But not all usages of such traceable e-mail are honorable. For example, if a spammer send you an HTML-based email and, in the course of opening it, you retrieve an image from the spammer's Web server, then the spammer is automatically tipped off to the fact that he or she found an active e-mail address. To ward off such malicious acts, most e-mail clients now offer the option of disabling automatic image retrieval when emails are opened. But, there's a problem in the way that Outlook 2003 and Outlook Express (the most popular e-mail clients in usage today) do this.
This "gap" in protection, which leaves users to cumbersome workarounds and third-party products to solve the PattyMail problem opens up the question of whether users of Outlook deserve a fix from Microsoft now or must they upgrade to Outook 2007 when it comes out? I spoke with a Microsoft spokesperson earlier today and she's looking into the matter. If anything comes of it, I'll let you know.