Google engineers claim that Chrome PWN bug is a Flash bug

Yesterday I reported that security firm VUPEN claimed to have a Google Chrome browser exploit that bypassed the browser's sandbox and Windows ASLR and DEP security measures. Today Google engineers are claiming that the bug isn't with Chrome itself but in the Flash player bundled with the browser.
Google security engineer Tavis Ormandy had this to say on Twitter:
"As usual, security journalists don't bother to fact check. VUPEN misunderstood how sandboxing worked in chrome, and only had a flash bug."
Side note: To be fair to security journalists, VUPEN doesn't given them much to go on, and only discloses details of the vulnerability to government organisations and 'paying' customers.
Another Google security engineer, Chris Evans, chimed in with this in a reply to another comment on Twitter:
"It's a legit pwn, but if it requires Flash, it's not a Chrome pwn. Do Java bugs count as a Chrome pwn too, because we support NPAPI?"
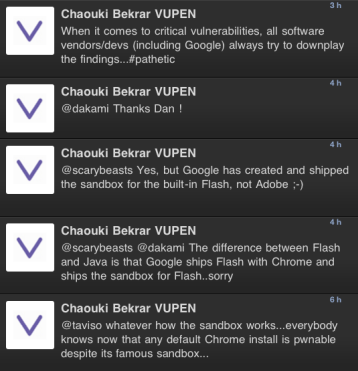
VUPEN, while being open to questions, isn't answering questions related to the bug. VUPEN CEO Chaouki Bekrar became involved in the conversation with Google engineers on Twitter.
Judging by his responses, I think that it is fair to say that this is indeed a Flash bug and not Chrome bug.