Ubuntu Lucid Lynx 10.04 can read your iPhone's secrets

Do you have a PIN code on your iPhone? Well, while that might protect you from someone making a call or fiddling with your apps, it doesn't prevent access to your data ... as long as the person doing the snooping around is using Ubuntu "Lucid Lynx" 10.04.
Security experts Bernd Marienfeldt and Jim Herbeck discovered something really interesting when they hooked up a non-jailbroken, fully up-to-date iPhone 3GS to a PC running Lucid Lynx ...
I uncovered a data protection vulnerability [9], which I could reproduce on 3 other non jail broken 3GS iPhones (MC 131B, MC132B) with different iPhone OS versions installed (3.1.3-7E18 modem firmware 05.12.01 and version 3.1.2 -7D11, modem 05.11.07) , all PIN code protected which means the vulnerability bypasses authentication for various data where people most likely rely on data protection through encryption and do not expect that authentication is not in place.
This is what you get via an auto mount without any PIN request:
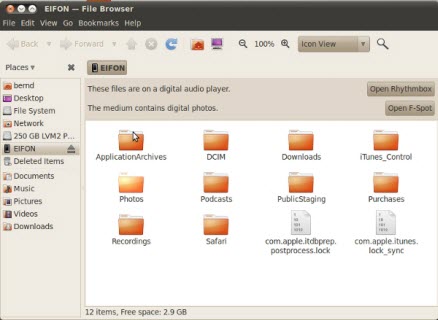
This data protection flaw exposes music, photos, videos, podcasts, voice recordings, Google safe browsing database, game contents… by in my opinion the quickest compromising read/write access discovered so far, without leaving any track record by the attacker. It’s about to imagine how many enterprises (e.g. Fortune 100) actually do rely on the expectation that their iPhone 3GS’s whole content is protected by encryption with an PIN code based authentication in place to unlock it.
This, quite honestly, is a staggering flaw. It basically allows anyone capable of driving a Linux PC to copy data off of an iPhone without the owner of the phone having any idea whatsoever that this has happened.
What's more worrying is that Marienfeldt and Herbeck think that write access to the iPhone is only a buffer overflow away, which means serious access.