Expert: Skype calls nearly impossible for NSA to intercept

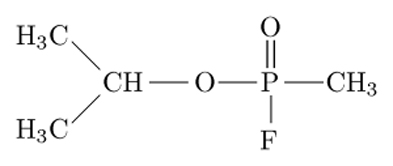
That's the formula for sarin, a deadly gas said to be a favorite of terrorists.
So let us say you have a terrorist in Amman, Jordan talking to a compatriot in Hamburg who has a line on some guy who trades in deadly chemicals, toxins, or naughty biowarfare agents.
And let us say they then dial up another compatriot in New Jersey.
If these calls are being made over Skype the conversations are being encrypted by 256-bit long Skype encryption keys are a length that at least in theory, would take a literal eternity to crack.
The National Security Agency may not be able to intercept them. Or even know that they are going on.
That's according to Bruce Schneier, chief technology officer at Counterpane Internet Security.
Schneier tells the AP's Peter Svensson that even if Skype's encryption is weaker then believed, it would still stymie the type of broad eversdroppoing that the National Security Agency is said to be performing. That eavesdropping is believed to involve scanning up to millions of calls at a time for certain phrases.
Even a weakly encrypted call would force an eavesdroopper to spend hours of computer time cracking it, adds Svensson via Schneier.
Skype's chief security officer Kurt Sauer tells Svensson that there are no "back doors" that could let a governmentpass the encryption on a call. He does add, however, that the company complies with all government requests in this area.
But my question is, what if the government- the NSA or whatever, doesn't know that these terrorists are talking over Skype because they cannot intercept the call?
Scary.