DDoS Attacks: Size doesn't matter

People often think that Distributed Denial of Service (DDoS) attacks-you know like the ones that knocked the Department of Justice, the Recording Industry Association of America (RIAA), Motion Picture Association of America (MPAA), and Universal Music recently--require hundreds of attackers generating gigabytes of traffic per second to pound a Website down into the ground. Ah, no they don't.
A DDoS attack can blast a site off the Web with a mere trickle of traffic. As Radware, a global application delivery and application security company for virtual and cloud data centers, just pointed out in its "2011 Radware Global Application & Network Security Report," smaller, less intensive attack can cause more damage than DDoS attack tools that gobble ten times the amount of bandwidth.
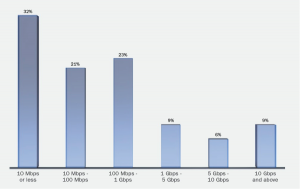
How small? Radware's Emergency Response Team (ERT) found that the majority of successful DDoS attacks were made with less than 1 Gigabit per second (Gbps). Sure, some attacks, like the one that got WikiLeaks in 2010 used 10Gbps level attacks, but, really, you don't need to that much traffic to knock the stuffings out of a Web site.
Other successfull DDoS attacks work by devouring server resources. That means it's possible for a successful DDoS raid to be made no matter how much bandwidth you have because it attacks your servers' resources. To really protect a network against attacks, both your Internet connection and your servers need defenses. Usually, DDoS attacks are aimed at your network's TCP/IP infrastructure. These assaults come in three varieties: those that exploit weaknesses in a given TCP/IP stack implementation; those that target TCP/IP weaknesses; and the tried and true brute force attack.
For example, Radware found that "the type of attack is also significant. A much smaller HTTP flood on the application level may do more damage than a larger UDP flood on the network. When evaluating DDoS attacks it is important to understand both the size and type of attack." In short, size alone doesn't matter as much as you might think. You're far more likely to be hit by a smaller, but potentially deadlier attack.
Radware also found that Firewalls or intrusion prevention systems (IPS) alone can't stop DDoS. Indeed, the firewall is the often weakest link. Radware found that in 32 percent of DDoS attacks, the firewall or IPS became the breaking point. To stop DDoS attacks you need dedicated hardware solutions, not IPS and firewall technologies.
While Content Delivery Network (CDN) providers can protect a business against the less sophisticated, large-volume attacks by simply absorbing them, but they won't slow down more sophisticated attacks. Indeed, even high-volume attacks can break through if the attacker randomly changes Web page requests. That DDoS technique, for example, was used recently to knock out Israel's Tel Aviv Stock Exchange and El Al airline. In these cases, the CDN just forwards all the attacks directly to the customer's servers. As Radware puts it this in essence makes "the CDN act as a proxy unloading the attack traffic directly at the target servers."
In a blog posting, Radware observes that there are several DDoS myths. The first, of course, is that organizations need to prepare for enormous attacks. The company notes that not only were 76 percent of attacks were less than 1Gbps in bandwidth, with 32 percent less than 10Gbps, only nine percent of attacks in 2011 were over 10Gbps.
Another myth is that "the proper way to measure attacks is by their bytes-per-second (BPS) and packets-per-second (PPS) properties. If the number of packet is high, the attack is more serious. Following this logic, a 10Mbps UDP flood would be more severe than a 5Mbps HTTP flood, which is not necessarily true"
They continue, "While enormous DDoS attacks are really about network flood attacks, the majority of organizations, which are targeted by sub 1Gbps attacks are targeted with a mix of network and application flood attacks. The impact of application flood attacks are much more severe than the network flood attacks - it is much easier to detect and block a network flood attack (which is about sending a large volume of irrelevant traffic such as UDP floods, SYN floods and TCP floods, typically spoofed) rather than an application flood attack where the attackers are using real IP addresses from real machines and running complete application transactions - it's the users which are not real."
So what can you do about this? Radware makes the following recommendations.
- Collect information about attacks such as type of attacks, size and frequency. Use the correct measures for the attack type. For example, the proper measurement for UDP floods is in bandwidth and PPS, while the measurement scale for HTTP floods is in transactions per second, concurrent connections, and new connections per second.
- Perform risk analysis at business level to determine the budget you should allocate to improve your business resilience against DDoS attacks.
- For bandwidth saturation attacks, make sure your service provider can mitigate volumetric attacks that may saturate your bandwidth.
- For application attacks, deploy anti-DoS and network behavioral technologies on site.
- Have a consolidated or "context aware" view into enterprise security with a security event information management (SEIM) system. An SEIM system can build a centralized architecture that simplifies such tasks as monitoring the millions of messages and log records generated by security.
By this time you've probably figured out that stopping a DDoS attack, big or small, isn't easy. You're right. It's not. Simply throwing more bandwidth at the problem isn't enough. You need to really analyze what's happening with your Web sites and Internet connection.
Think this can't happen to you? That DDoS attacks are only aimed at big companies or organizations with big enemies? Think again. Radware found that "In half of the attacks, companies did not know why they were targets. 'Hacktivists' with a political agenda accounted for [only] 22% of the attacks; 12% came from angry users; 7% from the competition and 4% wanted a ransom in exchange for freeing the website." The others? We don't know.
Worse still, Radware found that DDoS attacks became much more organized, professional and complex in 2011 with attackers using as many as five different attack vectors in a single attack campaign. No one point security tool could effectively block this sophisticated multi-level type of attacks. What is needed is a cocktail of techniques that together provide full protection."
I wish I could tell you something sweet and reassuring like "You're probably going to be fine." But, I can't. I've predicted for a while now that DDoS attacks would become only more common. They have, and they'll continue to happen more often. Like it or not, if you have a serious Web site, you're going to need to invest in serious DDoS protection for it. Good luck.
DDoS Traffic volume image courtesy of Radware.
Related Stories:
How Anonymous took down the DoJ, RIAA, MPAA and Universal Music Websites
How to try to stop DDoS Attacks
DDoS: How to take down WikiLeaks, MasterCard or any other Web site