A secure Wireless LAN hotspot for anonymous users

This information is also available as a TechRepublic PDF download.
As ubiquitous and convenient as Wireless LAN Hotspots are, it is probably the single most dangerous technology to the mobile computer user. From a security standpoint it is an absolute nightmare because of multiple inadequacies. The two biggest issues with Hotspots is that you have no idea if you're connecting to a legitimate Access Point or if you're connecting to a hacker's fake Access Point and everything you send and receive is transmitted in clear text with no encryption.
Anyone who doubts that this is a problem should ask themselves if they would post their email account passwords in my talkback section at the bottom of this blog or go in to an airport and yell out their user account names and passwords as loud as they can. If the answer is no then they should be concerned with Hotspot security. If we look at Defcon's Wall of Sheep every year, a sucker is literally born every minute and this isn't because there were hard-core hackers breaking in to people's Wireless LAN connections. In fact the only thing there were doing was passively listen as users sent out their usernames and passwords in clear text over the radio waves and posted the results on the Wall of Sheep. Of course we can always expect users to use some form of a VPN solution and encrypt everything going over the air but the vast majority of hotspot users don't do that and even when they do use VPN it doesn't necessarily encrypt all traffic.
Hotspots face the classic convenience and usability versus security tradeoff and 999 out of 1000 times the Hotspot will choose convenience and usability. The last time I used a secure Wireless LAN hotspot was at RSA 2007 and they proved why the security without the convenience is utterly unusable. This year at least they tried to make it a little easier than RSA 2006 by giving out anonymous usernames and passwords (instead of personalized accounts) but they still up running a line 20 people deep with a three-man helpdesk helping people set up their secure Hotspot access at the RSA conference. It must have wasted a thousand man-hours between the helpdesk and the users that had to wait in line. For this reason, no one bothers setting up a secured Hotspot and users won't use it even if they did because it would be too much trouble acquiring a username and password. But does it really have to be this way?
I have seen hotspots that use WPA-PSK (Wi-Fi Protected mode using Pre-Shared Key) to offer some level of privacy, but that's only private against people who don't have access to the PSK. Microsoft for example hosts conferences using WPA-PSK by handing out USB keys with automatic client configuration and a complicated random string used for the PSK. Even ignoring the fact that you need to physically give something to each guest for them to be able to make the connection, this mode of security can be snooped by anyone with access to the PSK because they can sniff and decode the decryption key during the initial setup of a WPA-PSK connection.
But there is actually a better and easier way to set up a secure Wireless LAN hotspot for an anonymous user using a single generic and common username and password that anyone can remember. An interesting property of PKI is that it allows us to do a secure key exchange without any usernames or passwords so long as one side has a trusted digital certificate. This concept is used millions of times a day by ordinary users anytime someone goes to an SSL-secured webpage and the secure authentication channel is set up before the user enters a username and password. The same general concept could be applied to the Wireless LAN world with a slight twist in the implementation.
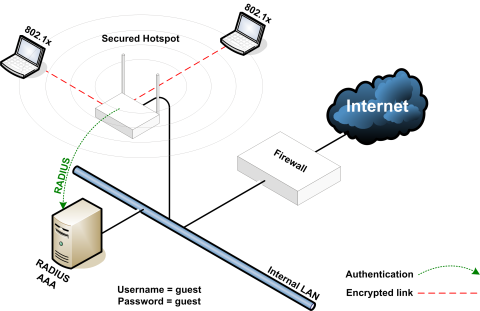
An interesting feature of Wireless LAN security using 802.1x and PEAP mode is that it is possible to log in with the same anonymous guest account with a publicly known password for any number of people and still provide each user with a secure point-to-point link-layer encryption. That means that someone with full knowledge of the anonymous guest user account and password will not be able to eavesdrop on any user that uses this hotspot system. So even if everyone in the world knows the username is "guest" and the password is "guest", they'll have connectivity to the network with more privacy than a typically unencrypted wire connection.
To implement this solution, we can do this with any typical Wireless LAN Access Point and a RADIUS server (how to set one up). So long as the connection between the Access Point and RADIUS server is secure or there is a sufficiently complex RADIUS secret, each wireless client has complete privacy. In this case since it's such a simple implementation, the RADIUS server could be embedded in to the Access Point itself which means you don't even have to worry about the RADIUS secret strength. The RADIUS server does however need a publicly trusted Digital Certificate (how-to guide here) which you can purchase for $20 at places like GoDaddy.com and there's literally zero difference between that and the $200 Certificates from other Certificate Authorities. Going with an in-house or self-signed Digital Certificate for this particular application isn't appropriate because external users have no trust relationship with your in-house Certificate Authority or your self-signed Digital Certificate and there is no easy way to automate that trust relationship like you can for internal users.
A RADIUS server is typically connected to a backend user directory such as Microsoft Active Directory, Novell, or LDAP but this particular application doesn't require that since we only need a single user account. We can set up a local user in the RADIUS server named "guest" with the password also set to "guest" which is extremely generic and easy to remember. That means when the user connects to this secured Hotspot, they will have to do an initial 802.1x/PEAP setup where they enter in the username and password. Since the credentials are so easy to remember, it's possible to do a quick-and-dirty setup guide for Windows and Mac with no complicated keys to remember or personalized user credentials. Fortunately, the guest credentials and the entire setup process can be saved for future use and the fact that it's so generic means that it can be applied consistently on a very large scale. Anyone looking to implement an easy to use and secure Wireless LAN Hotspot should seriously consider this solution.