Critical Broadcom Windows driver exploit released!

The MoKB (Month of Kernel Bugs) project has released a Metasploit 3.0 kernel-level driver exploit for Broadcom based Wireless LAN devices for Windows 2000 and XP. The flaw was discovered by researcher "Johnny Cache" and had been privately disclosed to Broadcom so that they could prepare a fix before the details of the research and proof-of-concept was released in to the public. [UPDATED 11/13/2006 7:00PM - PC makers like Dell, HP, Gateway, Fujitsu, eMachines, other computer manufacturers and others third party Wi-Fi card adapters are affected by this flaw. A simple way to determine if you have an affected Wireless driver is to do a file search for the BCMWL5.SYS file on your system partition which is usually the C drive. Any version of that file below 4.100.15.5 is vulnerable and you can find that information by right clicking on BCMWL5.SYS and selecting "Properties"]
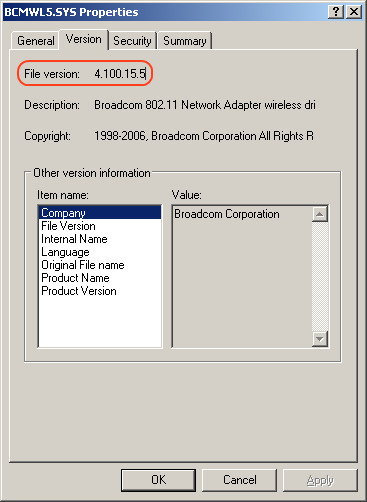
Broadcom created an updated reference driver but opted not to issue a security advisory. At this point in time, Linksys (division of Cisco) has released an updated driver that addresses this critical flaw though no indication of the critical nature of this update was given. [UPDATED 11/13/2006 7:00PM - Broadcom has informed me that HP issued a Windows certified driver to Windows Update in October for all HP and Compaq computers. HP users only need to go to Windows update under the hardware section and select the optional hardware driver update for their HP or Compaq-branded Broadcom wireless hardware. Venders like Dell, Gateway, Fujitsu, eMachines, and others have not issued updated drivers at this point but I have tested the Linksys drivers on my own laptop (which uses a Dell 1450 802.11 a/b/g miniPCI adapter) and the Linksys drivers work. The driver installation process is not straight forward since you are technically installing the wrong product drivers. But given the critical nature of this flaw, the Linksys branded driver can provide immediate protection until the correctly branded drivers are released. You can follow the step-by-step procedure below.
According to Johnny Cache, this particular exploit is extremely reliable and results in "100% ownage" which means your computer belongs to the hacker if it's attacked using this exploit. Since the exploit has been rolled in to the Metasploit 3.0 framework which includes kernel-level shell code, the exploit can be performed with a moderate amount of hacking knowledge. This flaw is extremely dangerous because it exploits the kernel of the operating system which means it bypasses all conventional security measures like anti-virus, HIDS, firewalls, and user privileges. The attack range is limited to Wi-Fi range which is typically 100 to 200 feet but can be extended with high-powered antennas.
It is unfortunate that the hardware manufacturers are keeping such a low profile for a critical flaw of this nature and Broadcom doesn't directly provide patched reference drivers. Intel was more responsible when it provided critical driver updates directly to the end user back in September so that the customers don't have to wait for their laptop manufacturer to provide updated drivers. If you haven't updated your Centrino wireless drivers yet, you should do so ASAP and use this guide to upgrade. For Broadcom chipset users which include Dell and HP branded Wi-Fi chipsets, I have created this emergency step-by-step procedure to install this critical driver update even if you're not using Linksys.
Emergency Broadcom Wi-Fi driver update procedure
[UPDATED 11/13/2006 7:00PM - HP users can use the optional driver update in Windows Update] Any one using a Broadcom Wi-Fi chipset can use this Linksys-branded driver from Linksys. The driver is labeled "WPC300N Wireless-N Notebook Adapter" but Johnny Cache tested the drivers on his Zonet 802.11 b/g cardbus adapter and I tested the Dell 1450 802.11 a/b/g miniPCI adapter. According to Cache, the exploit no longer functions with this particular driver which is good news.
The driver is about 13 megabytes but you only need the raw driver folder which is actually only 680 KB compressed. It would have been nice if Broadcom would provide a simple raw-driver update for their products but the bloated Linksys drivers are better than nothing and IT departments can distribute the tiny driver folder internally with ease. Once you've downloaded the drivers, use the self-extracting file to decompress the drivers on to your hard drive so you can get a copy of the drivers folder. You can delete the rest of the files if you're using the Windows XP SP2 wireless supplicant (AKA client) or some other wireless supplicant. The flaw according to Johnny Cache is localized to the driver itself so that's all you need to update.
Once you have the driver folder handy, go to the Windows Control Panel, then "Administrative Tools", and then "Computer Management". You can also get to it by right clicking on "My Computer" and clicking "manage". Click on "Device Manager" and follow the screen shots below.
You'll need to find the appropriate network adapter and right click on it. In my case, I chose the Dell Wireless 1450. Right click on it and hit "Update Driver".
Skip the device detection process and hit "Next".
Choose "Install from a specific location" and hit next.
Choose "Don't search, I will choose the driver to install"
Click on "Have Disk".
Use "Browse" to find the location of the updated drivers.
For Windows 2000, you'll have to get the latest official branded drivers from your Wi-Fi card or laptop maker. I will contact Broadcom and see if I can provide a complete list of affected products since it may be difficult to identify products that don't explicitly specify they are Broadcom based. If you're not comfortable performing these operations and you're not sure if you have a Broadcom adapter, don't perform this emergency update. These driver update instructions are provided as is with no guarantee on accuracy or effectiveness.
Yes this is an UGLY solution but it's all we have at this point. Broadcom should have provided certified drivers to Microsoft for inclusion in Windows Update but they didn't. But even then, Microsoft device driver updates are never pushed out as automatic critical updates and we all know that if it isn't automatic and seamless it probably won't get done. This is something Microsoft needs to address with the PC industry in general because driver exploits are becoming very common and very dangerous.