A U.S military botnet in the works
Make botnets, not war? In April, last year, I asked the question "Why establish an offensive cyber warfare doctrine when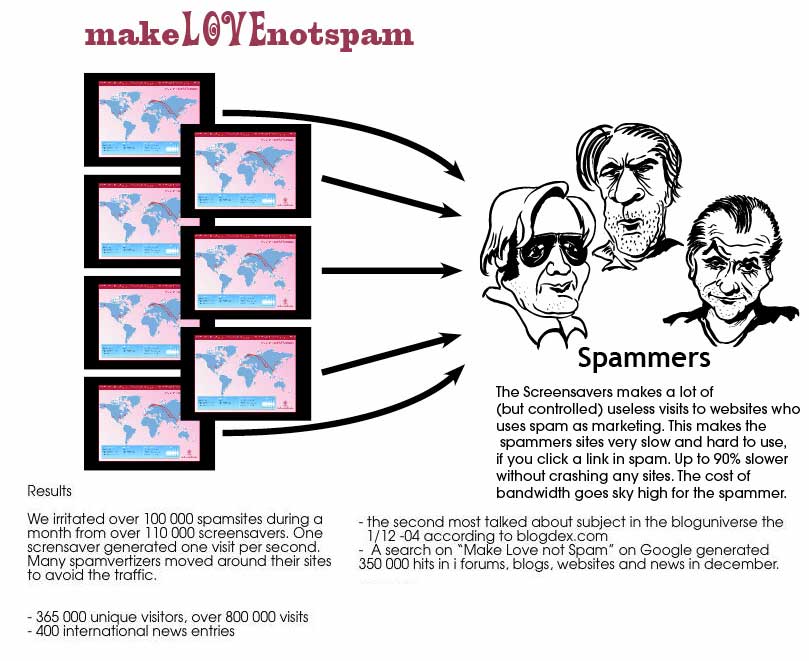
A year later, the U.S military is catching up on the concept, and with its current inability to utilize people's information warfare, is speculating on a .mil hosts only botnet as an offensive cyber warfare capability. Sarcasm is also following, with suggestions for Air Force 4-1-9 scams, and Dot mil phishing attacks. The controversial botnet idea leads us back to the Make Love Not Spam campaign, which was perhaps the most successful people's information warfare campaign to date, DDoS-ing known spam sites.
Quote from a related article :
"America needs the ability to carpet bomb in cyberspace to create the deterrent we lack," Col. Williamson wrote. America faces increasingly sophisticated threats against its military and civilian cyberspace. At the same time, America has no credible deterrent, and our adversaries prove it every day by attacking everywhere. Some people would fear the possibility of botnet attacks on innocent parties. If the botnet is used in a strictly offensive manner, civilian computers may be attacked, but only if the enemy compels us. The U.S. will perform the same target preparation as for traditional targets and respect the law of armed conflict as Defense Department policy requires by analyzing necessity, proportionality and distinction among military, dual-use or civilian targets. But neither the law of armed conflict nor common sense would allow belligerents to hide behind the skirts of its civilians. If the enemy is using civilian computers in his country so as to cause us harm, then we may attack them."
Protecting the "everywhere" is very marketable if you're a defense contractor pitching products and services to new hires, but reality is different, "everywhere" is a utopia by itself. Moreover, prioritizing the DDoS attack that would follow based on dual-use, civilian or military targets renders the entire idea pointless, since a DDoS attack could be launched from a foreign country's major unversity network, falling into the dual-use systems category. From a historical perspective, international adversaries are also known to enjoy hiding behind "the skirts of the civilians", by building barracks next to schools, headquarters next to hospitals, or building a ghost infrastructure within the urban landscape, right under the nose of civilians themselves, used as bites and insurance for causing complexity in any upcoming attacks.
Some issues to consider:
- cyber warfare tensions engineering in the sense of making it look like a specific country is attacking the U.S military in order to have the U.S military DDoS the country on behalf of the malicious parties, a fully realistic scenario given the huge number of malware infected hosts and the bad guys Geolocation capabilities
- with the number of netblocks prone to IP spoofing, there's no accountability on who's attacking who if someone wants to achieve the effect, well try everyone
- from another perspective the idea is both, ingenious and easy to render pointless if it is to include only .mil hosts within the botnet, mostly because a .mil tld extensions are descriptive enough to be blocked by default, and so are all the publicly known military netblocks
- knowing that the U.S military would DDoS back anyone attacking its networks creates opportunities for forwarding the execution of DDoS attacks to someone who's thinking they're under attack as botnets for hire consisting of of infected hosts from a specific country only are already pitched by botnet masters themselves
Here's one favorable comment of a reader :
"Whether or not we actually need a "botnet" to do it is inconsequential. DDoS attacks can be very useful when used in a coordinated IW attack on enemy communications and network infrastructure."
Where's the enemy, and where's the enemy's communications and network
The bottom line - why put efforts into building something that would generate a lot of negative publicity and might never materialize, when you can basically outsource the process and have the capability provided on demand? Just like the bad guys who do not have access to botnets do by using botnets as a service?