Apple bolsters QuickTime defenses... or do they?

A couple of great articles came out recently, one from Ryan Naraine and one from our very own Larry Dignan, about some of the defenses that Apple is trying to build into QuickTime to defend Vista users.
As we've talked about here before, with Vista, it's all about the DEP and the ASLR (ok, and SafeSEH, stack/heap canaries, etc.). DEP and ASLR is to Vista what "the clear and the cream" have been to Barry Bonds... ok, that's a low blow... to Microsoft. DEP and ASLR are neither illegal, nor have they made Microsoft's head bigger, whereas with Barry, well...
ASLR is really a great mitigation since exploits currently depend on known targets so that exploits can be reliable across a widespread audience. ASLR randomizes the address space of a process so that widespread exploitation is extremely difficult. The problem with ASLR is that it is an all or nothing proposition. If you have even one library that is not protected with ASLR in the process space, then it's game over (assuming the attacker can use that library to get back to shell code).
So I thought to myself today... did Apple get it right? I decided to go ahead and fire up LookingGlass, and look into it for myself. Unfortunately, I didn't have it on my corporate laptop, so I went over to David Maynor's Errata Security blog to go download, and what to my wondering eyes should appear, but a blog entry post that said "Maynor was here".
As Maynor mentions in his blog entry:
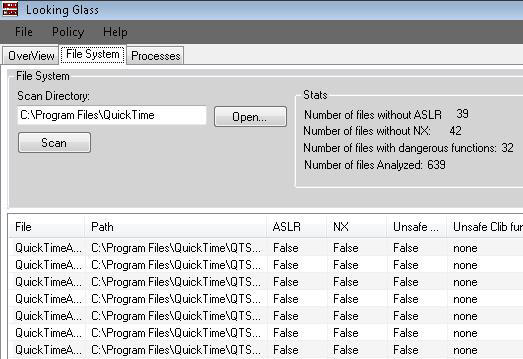
Although most of the files are now marked as ASLR enabled there are still a few binaries that are not and could still provide an attacker a static location to utilize.
Maynor provides a screen shot of LookingGlass being run against his updated install of QuickTime:
-Nate