Approximately 800 vulnerabilities discovered in antivirus products
UPDATE: McAfee debunks recent vulnerabilities in AV software research, n.runs restates its position. In what appears to be either a common scenario of "when the security solution ends up the security problem itself", or a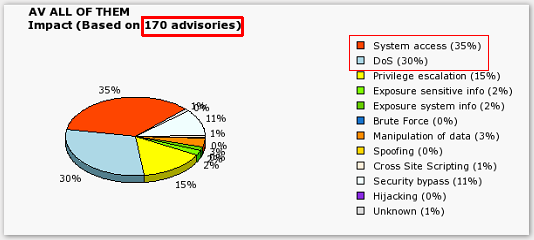
"During the past few months, specialists from the n.runs AG, along with other security experts, have discovered approximately 800 vulnerabilties in anti-virus products. The conclusion: contrary to their actual function, the products open the door to attackers, enable them to penetrate company networks and infect them with destructive code. The positioning of anti-virus software in central areas of the company now poses an accordingly high security risk. The tests performed by the consulting company and solutions developer n.runs have indicated that every virus scanner currently on the market immediately revealed up to several highly critical vulnerabilities. These then pave the way for Denial of Service (DoS) attacks and enable the infiltration of destructive code – past the security solution into the network. With that, anti-virus solutions actually allow the very thing they should instead prevent."
In between the ongoing efforts put by malware authors to obfuscate their binaries, release as many as possible in the shortest time frame achievable, or ensure that they bypass the most popular personal firewalls before releasing them by applying quality assurance to their malware campaigns, can antivirus products be a security issue themselves? But of course, and the increasing number of vulnerabilities discovered is clearly indicating the increasing interest in proving the point in general.
How did n.runs manage to discover the vulnerabilities they claim they found? By following the very same logic on which a great deal of the
"In this context, n.runs was able to make out so-called "parsing" as one of the main causes of this boomerang effect. The principle functions as follows: virus scanners must recognise as many "Malware" applications as possible – and thereby comprehend and process a large number of file formats. In order to be able to interpret the formats, an application must partition the corresponding file into blocks and structures. This separation of data into analysable individual parts is called "parsing". Mistaken assumptions in the course of programming the parsing code create constellations which enable the infiltration and subsequent running of programme code. Moreover, the quick reactions time expected by developers (regarding threats) contributes to a decrease in the quality of the code. In short: the more parsing that takes place, the higher the recognition rate and the degree of protection from destructive software, but at the same time, the larger the attack surface – which makes the anti-virus solution itself a target."
The research they cite is based on Secunia's tracking of advisories affecting antivirus products, as well as research conducted by the University of Michigan emphasizing on the severity of the vulnerabilities on a per product basis. For instance, between 2002 and 2005 there were 50 advisories regarding vulnerabilities affecting antivirus products, but between 2005 and 2007, there's been an increase of 240% with 170 advisories. Moreover, according to a research paper by Feng Xue, presented at this year's Blackhat Europe, according to the U.S national vulnerability database, 165 vulnerabilities within antivirus products have been reported during the last 4 years. It's even more ironic to point out that the now fixed remote code execution vulnerability in Panda Security's online virus scanner, further proves that the security solution can indeed end up the security problem itself.
With the increasing interest and success into finding critical security vulnerabilities within antivirus products, are we going to see more abuse of these "windows of opportunity" by malware authors themselves? I don't think so, at least not on a large scale. What they are going to continue researching are ways in which to shut down the antivirus solution silently, prevent it from reaching its hard coded update locations, and most importantly ensure the malware has been pre-tested against the most popular security solutions before it's released in the wild - precisely what they've been doing for the last couple of years.