Attacker: Hacking Sarah Palin's email was easy
"Hello, /b/ as many of you might already know, last night sarah palin’s yahoo was “hacked” and caps were posted on /b/, i am the lurker who did it, and i would like to tell the story. In the past couple days news had come to light about palin using a yahoo mail account, it was in news stories and such, a thread was started full of newfags trying to do something that would not get this off the ground, for the next 2 hours the acct was locked from password recovery presumably from all this bullshit spamming.
after the password recovery was reenabled, it took seriously 45 mins on wikipedia and google to find the info, Birthday? 15 seconds on wikipedia, zip code? well she had always been from wasilla, and it only has 2 zip codes (thanks online postal service!) the second was somewhat harder, the question was “where did you meet your spouse?” did some research, and apparently she had eloped with mister palin after college, if youll look on some of the screenshits that I took and other fellow anon have so graciously put on photobucket you will see the google search for “palin eloped” or some such in one of the tabs. I found out later though more research that they met at high school, so I did variations of that, high, high school, eventually hit on “Wasilla high” I promptly changed the password to popcorn and took a cold shower."
Originally blamed for the email hijacking, the Anonymous movement against the Church of Scientology has distanced from the hack :
"One of the main tenets of the anonymous movement against the Church of Scientology is to stay legal. Anonymous is no fixed group, just a term for anyone who acts without giving their name. We don't know who is responsible for the hack on Sarah Palin's mail account or what their attitudes to Scientology or anything else are. For us, they are anonymous, because we don't know who they are and they are not us."
Meanwhile, the owner of the Ctunnel.com service recently commented that if the attacker's screenshot didn't include the
It's also worth pointing out that in the time of posting this, Wikileaks.org's article on "Sarah Palin Yahoo account 2008" has been defaced with the following message, reminding us that Wikileaks has a "fan club" too :
"I NOW HACK THIS WEBSITE! AREN'T YOUR PROUD OF ME, WIKILEAKS. I CAN PLAY YOUR GAME TOO!!!"
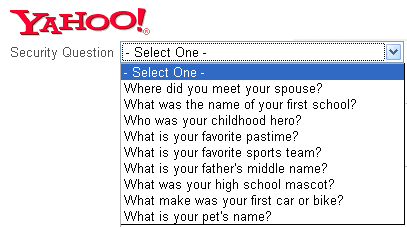
"Anyone that knows my address can easily figure out the name of my first school or my high school mascot. All of my neighbors, family and friends know both my dog’s name and my dad’s middle name, and everybody in the world knows I just LOVE the Lakers. As for my wife and me, the people who attended our wedding had the chance to hear about it in the ceremony - in case you couldn’t make it, we met on a roof of a bus, in Ladakh, India in 1994…
The fact that the answer to each of the security questions above is relatively easy to find out, makes them a security vulnerability in my Yahoo! account. By letting me make a security key based on the name of my first school, Yahoo! actually puts me at risk, allowing anyone that knows where I live to hijack my account. It’s like saying “We have the greatest lock to protect your house. Now, why don’t we hide the key under the mat”."
Hacking is supposed to be about intellectual exploration, so resetting the password of someone's Yahoo mailbox no matter if it's the Pope, requires no more than two brain cells put into action. However, the political consequences and the long-term impact of this hack are an entirely different topic yet to be discussed based on the interpretation of the data found within.