Comcast's DNS records hijacked, redirect to hacked page
For a couple of hours yesterday, Comcast's Internet Portal (comcast.net) had its DNS records hijacked and a defaced web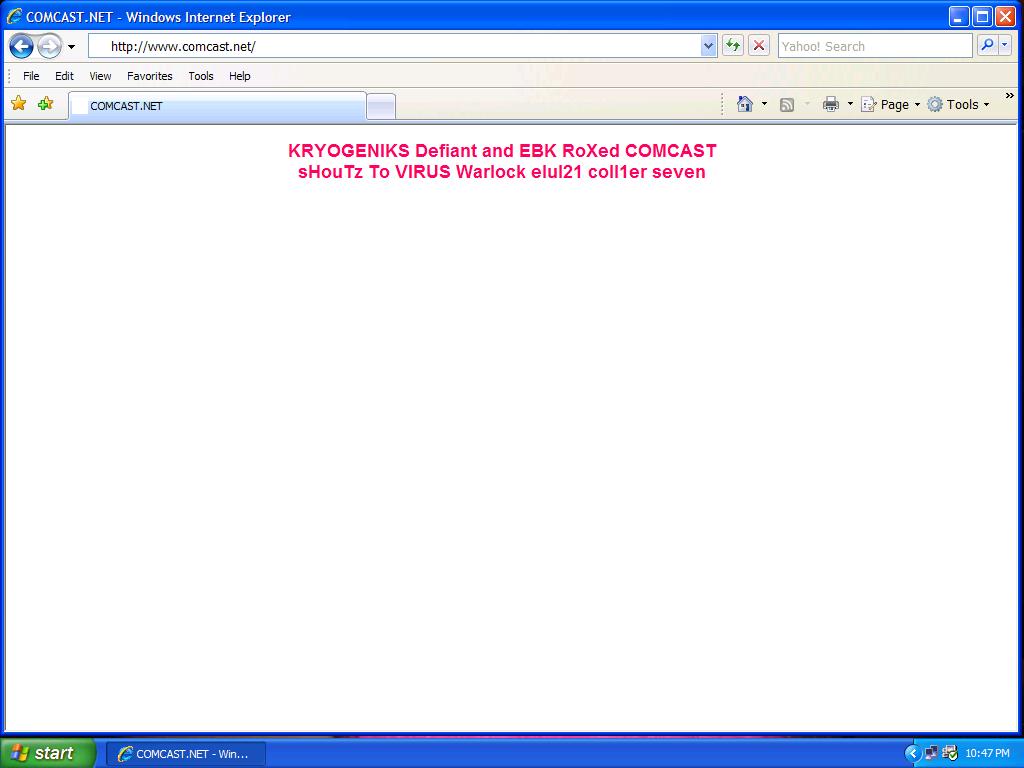
On 28-May-2008 23:05:43 EDT Comcast.net's WHOIS records were hijacked, and were returning the following information :
Administrative Contact: Domain Registrations, Comcast kryogenicsdefiant@gmail.com Defiant still raping 2k8 ebk 69 dick tard lane dildo room PHILADELPHIA, PA 19103 US 4206661870 fax: 6664200187
During that time, the page used in the defacement was loading from two different locations, namely, freewebs.com /buttpussy69 and freewebs.com /kryogeniks911 which continue returning the message :
KRYOGENIKS EBK and DEFIANT RoXed COMCAST sHouTz To VIRUS Warlock elul21 coll1er seven
Due to the changed DNS records, comcast.net was also unreachable for a certain period of time, and within the next couple of hours upon Comcast noticing the incident and taking actions to restore access to their domain, a "Web Site Under Construction" message was appearing.
Comcast's original DNS records returned the their original state on 29-May-2008 01:18:02 EDT :
Administrative Contact: Domain Registrations, Comcast domregadmin@comcastonline.com Comcast Cable Communications Mgmt. LLC One Comcast Center 40th Fl. PHILADELPHIA, PA 19103 US 215-286-8665 fax: 6664200187
The hijacking was also picked up by uptime monitoring services, with the longest downtime for the Comcast.net domain for the past three years (98.29%) or 18 minutes :
Tracking down the DNS hijackers using the message left, leads to the well known Kryogeniks group (kryogeniks.org) , elul21 (username.com/tmp) as another web site defacer part of the WINGS Hacking Team, next to CoLL1er.
Investigation is ongoing, details will posted once more data is gathered.