Conficker worm to DDoS legitimate sites in March
What if the Conficker worm suddenly decided that the phone-back locations for March were those of legitimate sites?
According to Sophos, during March, the millions of Conficker infected hosts will attempt to phone back to several legitimate domains, among which is a Southwest Airlines owned wnsux.com, potentially causing a distributed denial of service attack on all of them. Here's a list of the legitimate domains and dates on which Conficker will attempt to contact/potentially DDoS them:
Music Search Engine - jogli.com on 8th of March Southwest Airlines - wnsux.com on 13th of March Women's Net in Qinghai Province - qhflh.com on 18th of March Phonetics by Computer - praat.org on 31th of March
In an attempt to mitigate this attack, Southwest Airlines owned wnsux.com domains was modified yesterday and is no longer resolving to a particular IP. However, praat.org is a redirect to the University of Amsterdam's Institute of Phonetic Sciences and just like qhflh.com and jogli.com is still active.
The reverse engineering of the domain registration algorithm not only made it possible to anticipate the upcoming command and control locations, but also, allowed security companies to pre-register them and lock them under the Conficker Cabal alliance with members such as Microsoft and the ICANN. Moreover, perhaps the most pragmatic mitigation solution implemented on a large scale so far, has been OpenDNS updated Stats System which automatically stops resolving Conficker's latest domains, a feature which they introduced last month.
For the time being, the Conficker botnet remains in a "stay tuned" mode with the real malicious payload to be delivered at any particular moment. A patch has been available since October, 2008.
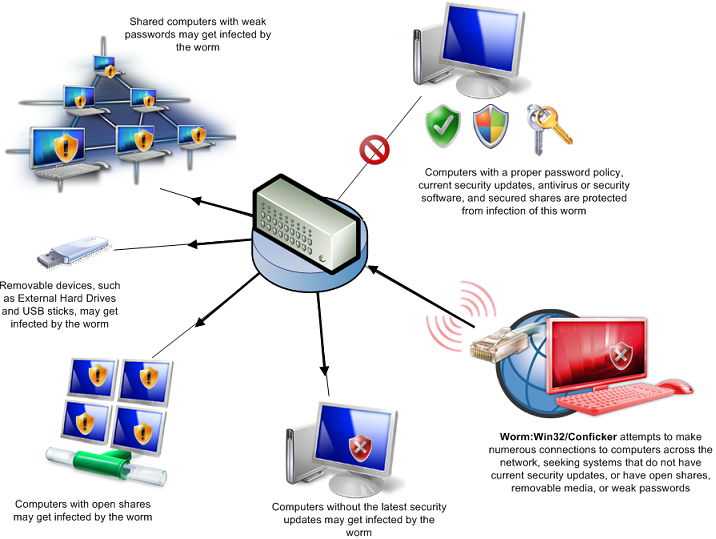
Conficker graph courtesy of Microsoft's Malware Protection Center.