Cross-platform malware exploits Java to attack PCs and Macs

Security vendors have discovered a new piece of malware that attacks both PCs and Macs. It uses the same Java security vulnerability exploited by the Flashback malware that infected hundreds of thousands of Macs. While the attack vector is the same as in Flashback, this Java applet checks which OS it is running on and downloads suitable malware for it.
Malware writers love using a cross-platform plugin as an attack vector because it allows them to target more than one operating system, and thus more potential users. Since Java has been having security problems for a while now, it shouldn't be too much of a surprise it is now being used in an attack targeting both Windows and Mac computers.
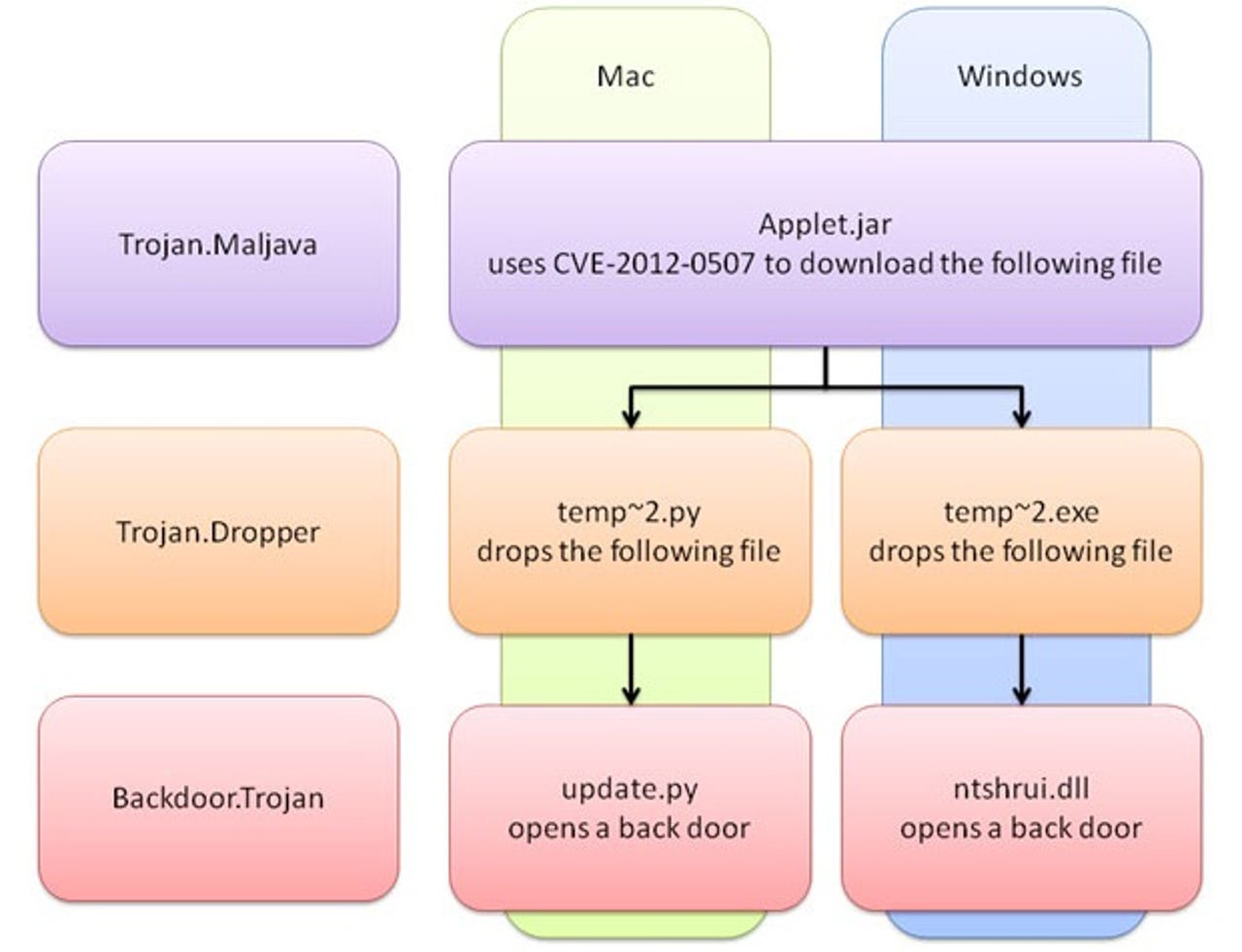
This particular malware exploits the Java vulnerability to download further malicious code onto your computer, as you can see above. A backdoor Trojan written in C++ is installed on Windows while a similar Trojan written in Python called update.py (extracted from install_flash_player.py) is installed on Mac OS X.
Both droppers result in a Trojan that opens a back door on the compromised computer, allowing remote hackers to secretly send commands, upload code to the victim's computer, steal files, and run commands without the user's knowledge. The two Trojans are downloaded from the same server.
The Trojan only checks whether it is running on Windows once, but the downloaded Python dropper checks again whether it is running on a Mac or not. If it is running on Linux or some other operating system, the threat does nothing. Python is not often used to write malware, but in this case it works fine on Macs since Python is installed by default.
The Mac one can control how many times it gets commands from the server at certain time intervals (polling times), in order to avoid IDS or IPS detection. The network connection is also encrypted by RC4 or compressed by Zlib. The threat has the following functions: download files, list files and folders, open a remote shell, sleep, upload files.
In addition to using an antivirus, you can check if your Mac is infected by looking for these two files (both can be safely deleted):
/Users/Shared/update.sh (shell script) /Users/Shared/update.py (Python script)
The Windows one sends the following information back to the remote attacker: CPU details, Disk details, Memory usage, OS version, and user name. The Trojan can also download a file and execute it, or open a shell to receive commands.
Patches for this Java vulnerability have been available since February 14 for Windows, Linux, and Unix computers. Apple released a patch in early April, before the Flashback botnet was discovered. Apple has not issued a Java security update for users running versions of Mac OS X prior to 10.6 (Snow Leopard) because it wants to upgrade to a newer version of its operating system. These users can only protect themselves by disabling Java.
If you don't use Java, you also should disable it. Even if you don't have it installed, always get the latest security updates for your operating system and software, whether it's from Microsoft, Apple, or any other company.
For reference, Sophos detects this threat as Mal/20113544-A and Mal/JavaCmC-A. Symantec detects the Java Applet malware as Trojan.Maljava, the droppers as Trojan.Dropper, and the back door Trojans as Backdoor.Trojan.
See also:
- New Flashback variant silently infects Macs
- New version of Mac OS X Trojan exploits Word, not Java
- New targeted Mac OS X Trojan requires no user interaction
- Over 600,000 Macs infected with Flashback Trojan
- Russian security firm says Flashback infection rates still high
- How big a security risk is Java? Can you really quit using it?