DIY phishing kits introducing new features
With the overall availability of phishing pages which phishers constantly update to keep track of the brand's changing login pages, phishing pages for every brand and financial institution can be easily perceived as a commodity good in the underground market. This trend is directly ruining the entry barriers into the phishing market segment, allowing novice phishers to use the very same scam pages, professional phishers once used to.
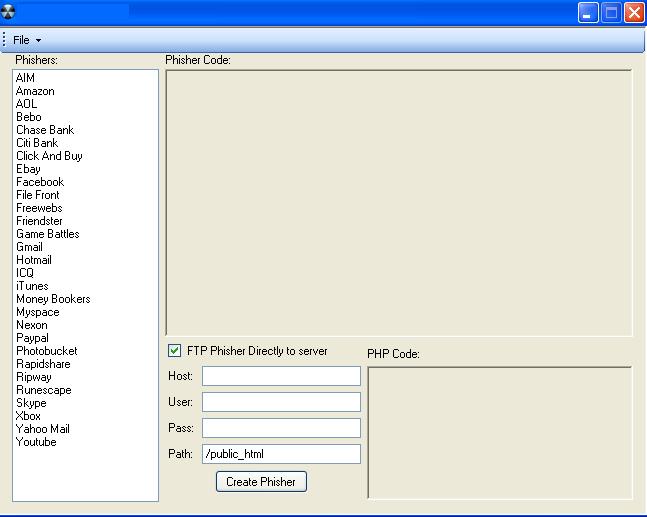
The DIY phishing kits trend started emerging around August, 2007, with the distribution of a simple kit (screenshots included), whose objective was to make it easy for a phisher already possessing the phishing page, to enter a URL where all the data would be forwarded to. Several months later, the kit went 2.0 (screenshots included) and introduced new preview, and image grabber features in order to make it easier for the phisher to obtain the images to be used in the attack.
In early 2008, two more phishing kits made it in the wild, with the first once having direct FTP upload capabilities as well
AIM, Amazon, AOL, Bebo, Chas Bank, City Bank, Click and Buy, Ebay, Facebook, File Front, Freewebs, Friendster, Game Battles, Gmail, Hotmail, ICQ, iTunes, Money Bookers, Myspace, Nexon, Paypal, Photobucket, Rapidshare, Ripway, Runescape, Skype, Xbox, Yahoo Mail, Youtube
How does the Rock Phish kit, and botnets used as the primary distribution vectors fit into the picture? Just fine, given that custom tailored templates with the latest version of the login page is the foundation of any phishing campaign. Which also leads us to another perspective, namely, is someone getting successfully phished with the latest version of the original login page, or are they getting phished with an outdated one?
Key summary points:
- this ongoing competition among the kits' creators, would ultimately serve the average phisher, empowering her with access to both the pages, and the ability to tweak them, and make it easy
- the introduction of point and click upload functions is a great indication of features to come, in fact, knowing that Russian Business Network's infrastructure was participating in a phisher-in-the-middle attack is prompting me to "what if" known to be malicious and scammy infrastructure starts offering direct hosting access like the once introduced in the first kit
- now that templates can be easier to configure, monitoring of changes made to the original login pages, and integrating upload
- taking into consideration related security incidents where stolen FTP data was used to embed malicious iFrames at the affected servers, automating the upload process to take advantage of huge list of already compromised account data is prone to appear as a feature in the short term
Whereas for the time being phishing remains a passive attack on a large scale, the potential to evolve into a blended threat by default, including exploits that would
To sum up - phishing tactics are evolving, in fact phishing pages are already getting hosted on defaced web servers, SQL injected to forward the survivability of the page to the injected server, and worse of all - this is done efficiently and would continue to be done even more efficiently.