Home & Office
Evilgrade: Exploit toolkit pwns insecure online updates
A security research outfit in Argentina has released a malcode distribution toolkit capable of launching man-in-the-middle attacks against popular products that use insecure update mechanisms.The toolkit, called Evilgrade, works in conjunction with man-in-the-middle techniques (DNS, ARP and DHCP spoofing) to exploit a wide range of applications, according to a post on the Metasploit blog.

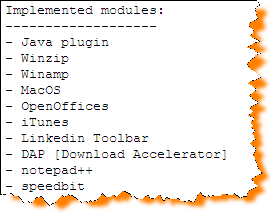
ISR-evilgrade: is a modular framework that allow us to take advantage of poor upgrade implementations by injecting fake updates. It works with modules, each module implements the structure needed to emulate a false update of specific applications/systems. Evilgrade needs the manipulation of the victim dns traffic.See more in this slide deck (pdf).