Exploit code published for RDP worm hole; Does Microsoft have a leak?

UPDATE: Microsoft confirms MAPP exploit code leak
Chinese hackers have released proof-of-concept code that provides a roadmap to exploit a dangerous RDP (remote desktop protocol) vulnerability that was patched by Microsoft earlier this week.
The publication of the code on a Chinese language forum heightens the urgency to apply Microsoft's MS12-020 update, which addresses a remote, pre-authentication, network-accessible code execution vulnerability in Microsoft's implementation of the RDP protocol.
It also sets of alarm bells in the corridors at Redmond because there are clear signs that Microsoft's pre-patch vulnerability sharing program has been breached or has suffered a major leak.
[ SEE: Microsoft makes daring vulnerability sharing move ]
The program, called MAPP ( Microsoft Active Protections Program), provides vulnerability data and triggers to anti-virus, intrusion prevention/detection and corporate network security vendors about 24 hours before the patch is released. The program provides detection guidance ahead of time to help security vendors reproduce the vulnerabilities and ship signatures and detection capabilities without false positives.
Microsoft says it has strict guidelines to ensure the data doesn't fall into the wrong hands but, in this case, my sources tell me the Chinese hackers had access to MAPP information even before the patch was released.
"I can say with 100% certainty that MAPP information got into the wrong hands," said a security researcher with access to the MAPP information.
[ SEE: Microsoft: Expect exploits for critical Windows worm hole ]
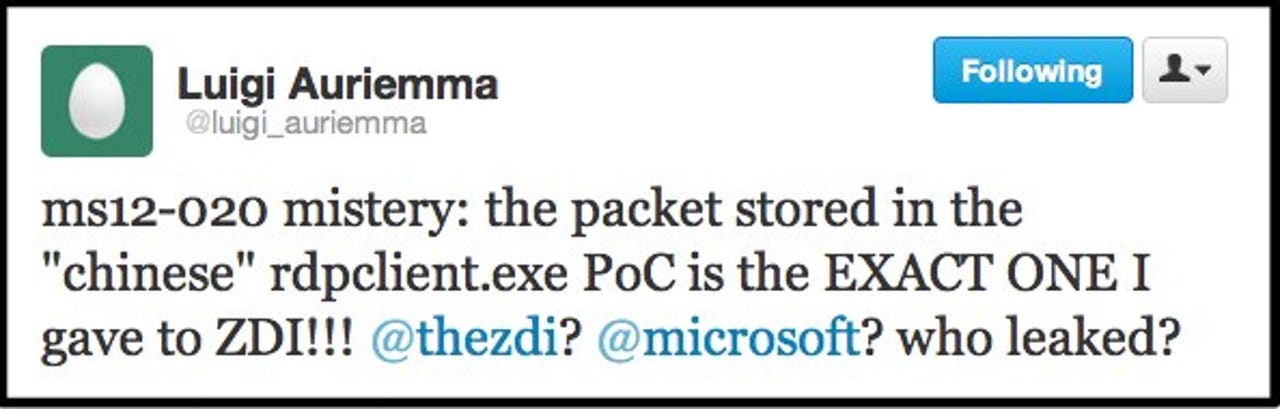
This was confirmed by Luigi Auriemma, the security researcher credited by Microsoft with finding and reporting the RDP code execution vulnerability. On Twitter, Auriemma said the a packet stored in the Chinese proof-of-concept was the "EXACT ONE" he provided to TippingPoint ZDI (Zero Day Initiative), the company that bought the rights to the bug information.
Auriemma suggest there was a clear leak somewhere along the line, publicly pointing fingers at Microsoft and ZDI.
In an interview, Auriemma told me there is no doubt whatsoever that the Chinese proof-of-concept came from Microsoft. "The packet I gave to ZDI wasn't just a simple fuzzed packet. I modified at some points to make it unique," he explained, noting that the Chinese code contained the packet "as is."
(click image for full size to see code snippet)
Auriemma said he never provided an exploitable proof-of-concept to Microsoft and speculates that the code was written by the MSRC to help during the triage and bug-testing process. But he's very clear that there's a leak (or breach?) at Microsoft.
"There are some parts that are not just some bytes modification. I did some unique things to make debugging easier. I referred to the BER numbers (numbers with a dynamic size). They were 8-bit originally and I converted them to 32-bit with the result that the packet increased its size. So, it's my packet," Auriemma said.
Officials from Microsoft and ZDI were not available for comment at press time.
A confirmed MAPP leak would be a big black eye for Microsoft because the program is considered a jewel in the company's efforts to secure the Windows ecosystem. In 2008, when the program was launched, I warned that it was a risky move because of the likelihood that information flowing through MAPP could be siphoned off and sold to malicious attackers.
At the time, Microsoft acknowledged the risk but insisted it would lock down access to the program and implement measures to identify potential leaks. Participants in the program must sign NDAs and have a significant enough customer base for protection-oriented software.
Following the publication of the Chinese PoC, which currently crashes vulnerable Windows installations, Auriemma published his own advisory with technical details of the vulnerability.
UPDATE: Microsoft confirms MAPP exploit code leak
* More to come...