Facebook introducing new security warning feature
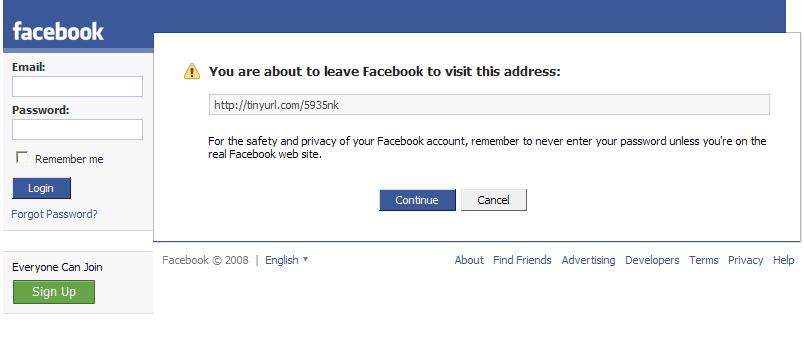
What Facebook's feature is doing, is simply adding a warning message to links it suspects of being spam or phishing like the following :
"You are about to leave Facebook to visit this address. For the safety and privacy of your Facebook account, remember to never enter your password unless you're on the real Facebook web site."
And if it wasn't Facebook's mentality of making it hard for spammers to spread their campaigns across the network at the first place, perhaps the only useful feature of the warning message is its potential to slow down an ongoing malicious campaign by making the user think twice before clicking further. Whereas the feature is a step in the right direction, it's still lacking some of the possible defenses whose implementation we would hopefully witness in the long-term, else it's just good PR. What could be improved anyway?
- process all outgoing links through a leading provider of web filtering solutions, in fact cost-effectively outsource the entire process
- integrate freely available blacklists of malicious and phishing sites such as, Google's Safe Browsing Diagnostic, SiteAdvisor, Phishtank, BrowserDefender and Norton's SafeWeb, then cross check the outgoing link through them and come up with a score for potential maliciousness
- implement URL shortening and highlighting of the original domain in order to expose a phishing email relying on numerous subdomains aiming to visually social engineer the user
- take notice from the competition and how Msplinks.com evolved during the last year thanks to all the cybercriminals finding ways to bypass it
As far as MySpace's Msplinks.com is concerned, the feature wasn't proactively introduced, but was implemented in a rather reactive move to several massive phishing attacks that were hitting MySpace at the time. By the time MySpace's Tom Anderson announced its release in April, 2007, malicious attackers started playing around with it, successfully finding ways to bypass it, with MySpace usually catching up with the technique several months after it's been available. The vision behind this centralization is the following according to Anderson :
"Hey everybody, we just launched another program to stop dirty spammers from hasseling [sic] you. When you input a link in myspace it may be converted to a redirect link. You’ll start seeing them around the site. They look like this: msplinks.com/adf9sd9f. These links are legit and we are creating them. They are not viruses or whatever else your conspiracy theorist friends told you. They still point to their original url, but let us easily turn off links to spam, phishing, or virus sites. booyah!"
Then in March, 2007, a large scale phishing attack prompted MySpace to start using msplinks not only on comments, but also, on profiles :
"Tonight we started using msplinks on profiles, just like we've been using them in comments. Whenever you save a url in your myspace page, we convert it to an msplinks url. This allows us to easily and instantly disable links sitewide. If a phishing link gets out into common use, we can turn it of instantly."
And despite that the move did slow down the phishing campaign, MySpace's msplinks is anything but perfect, with another massive phishing campaign that hit the social networking site in November, successfully getting around the redirector.
Cybercriminals adapt more often to a particular service's defenses in place than the service would like admit. While some are looking for ways to bypass the centralized redirector, opportunistic attackers are successfully finding ways to host the phishing profiles on the social network sites themselves. In times when the ongoing abuse of legitimate web services as redirectors or actual hosting providers of phishing and malware attacks is increasing, exposing your users wanting their "Web 2.0 experience" to already identified as malicious hosts shouldn't be the case.