Gmail, Yahoo and Hotmail systematically abused by spammers
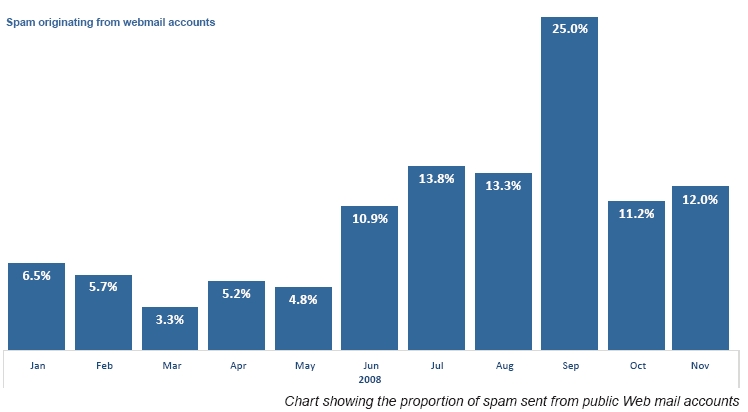
The latest MessageLabs Intelligence annual report for 2008 indicates that on average, 12 percent of the spam volume that they were monitoring in 2008 came from legitimate email providers such as Gmail, Yahoo Mail and Hotmail, followed by its September's peak of 25%. Earlier this year, more vendors emphasized on this ongoing development, citing machine learning CAPTCHA breaking techniques as the cause of it. In reality though, the very same humans that CAPTCHA was meant to identify continue undermining it as an anti-bot registration measure.
Researching the market segment throughout the year (Microsoft's CAPTCHA successfully broken; Gmail, Yahoo and Hotmail's CAPTCHA broken by spammers; Spam coming from free email providers increasing; Spammers attacking Microsoft's CAPTCHA -- again; Inside India's CAPTCHA solving economy) it's time to assess the current situation and speculate on the upcoming efficiency model.
"In 2008, spammers developed an affinity for spamming from large, reputable web-based email and application services by defeating CAPTCHA (Completely Automated Public Turing Test to tell Computers and Humans Apart) techniques to generate massive numbers of personal accounts from these services. In January, 6.5 percent of spam originated from these hosted webmail accounts, peaking in September when 25 percent of spam originated from these sources, averaging about 12 percent for the remainder of the year."
Is the supply of pre-registered accounts at these services driving the market, or is the customer's demand that's actually driving it? Whatever the case, supply is pretty efficient for the time being. For instance, I'm currently monitoring several web based bogus account registration services, with an average price for a thousand accounts at any of these email providers of $10. That's right, for $10 a spammer could get his hands on a thousand pre-registered email accounts if we are to exclude the discounts offered for a bulk purchase. And whereas I still haven't been able to establish a relationship between these services and Indian CAPTCHA breakers, theoretically, the supply of bogus accounts offered by a Russian service could be in fact outsourced as registration process to human CAPTCHA breakers, and the service itself acting as an intermediary. Whether it's the use of malware infected hosts, or through human CAPTCHA solvers, the hundreds of thousands of accounts offered for sale remain there.
"The presented vulnerability enables an attacker to bypass blacklist/whitelist based email filters and freely forge all fields in an email message by having Google’s SMTP servers tricked into behaving like open SMTP relays. We were able to confirm that this vulnerability is indeed exploitable by assembling a proof of concept (PoC) attack that allowed us to use one single Gmail account to send bulk messages to more than 4,000 email targets (which surpasses Gmail’s 500 messages limit for bulk messages). Although we have limited the number of messages in our example to 4,000+, no counter measures took place that would have prevented us from sending more messages, and for that matter sending an unlimited number of messages."
What this means is that the potential spamming speed achieved through a single automatically registered Gmail account could be greatly increased. From another perspective, a bogus account wasn't worth as much as it is worth today, since it allows automatic access to all of the company's web properties allowing spammers and cybercriminals (Cybercriminals syndicating Google Trends keywords to serve malware) to abuse them even further. CAPTCHA is dead, humans that were supposed to recognize it killed it by starting to recognize it efficiently and monetizing the process.
The bottom line, ask yourself the following - how many incoming anti-spam solutions can you think of right now, and how many outgoing anti-spam solutions are you aware of? Before spam comes it has to go out first.