Tech
Hacker demos how to defeat Citibank's virtual keyboard
A security researcher in India is warning that Citibank's new virtual keyboard anti-phishing mechanism can be easily defeated.

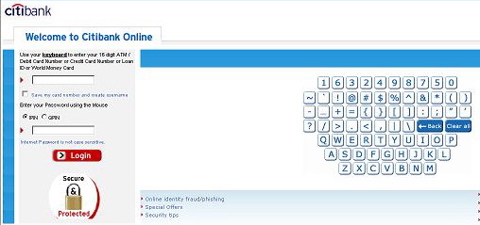
A security researcher in India is warning that Citibank's new virtual keyboard anti-phishing mechanism can be easily defeated.
The feature, which is offered to some international customers (it's not available in the U.S.) lets Citibank customers launch an onscreen keyboard to enter passwords.
The intent is to thwart the use keystroke loggers to hijack login credentials but, according to an advisory from a hacker known as Yash K.S., local attackers can circumvent the system to grab screenshots of sensitive user credentials.
He provided a proof-of-concept demo to show how a local attacker can use Win32 APIs to capture screenshots of usernames, passwords, credit card numbers, pin numbers and any other mouse clicks into the virtual keyboard.
In the example, the researcher showed how an executable placed on the victim's machine can be used to grab the screenshots and place them into a hidden directory. A call-home bot can then be used to transmit the virtual keystrokes from the hijacked machine to a remote server controlled by the attacker.