Hacker threatens to expose Anonymous members, Al Qaeda supporters

The Jester, a hacker who has caused trouble for other hackers before, claims to have exploited smartphones belonging to Islamist extremists, Al Qaeda supporters, Anonymous members, and LulzSec/AntiSec members. He says he elevated his privileges on each exploited device, extracted data, and stole address books, call logs, text message logs, and e-mails from targeted victims.
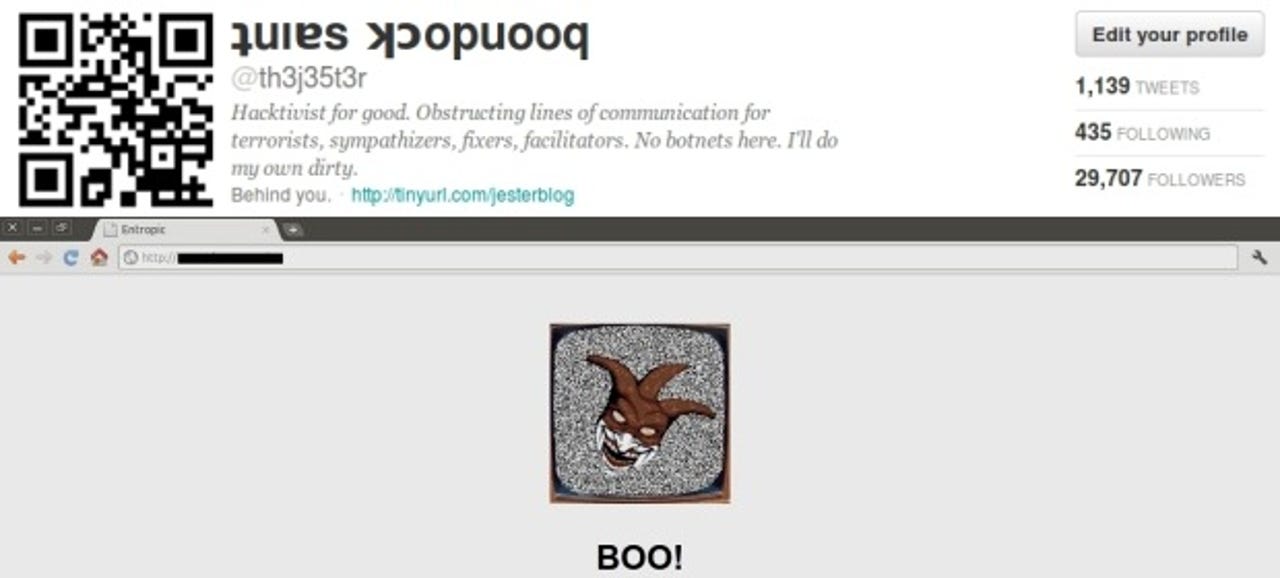
The Jester used his Twitter account (first picture above) to compromise hundreds of smartphones by changing his profile picture to a QR code over a five day period last week. When users scanned the QR code with their smartphone, a link opened in their browser, where an image of The Jester and the text "BOO!" appeared, according to Jester's Court.
In the background, The Jester exploited a vulnerability in the WebKit engine that powers browsers in Android and iOS. The Jester says he compromised the phones of 500 out of 1,200 individuals who scanned the code via a crafted webpage. He then stole personal data from a significant number of activists.
The security hole he claims to have used, CVE-2010-1807, has been in the public domain since November 2010 and has since been fixed in most browsers. Still, The Jester says he modified the exploit code slightly and still managed to see a 40 percent success rate, presumably on unpatched browsers.
The malicious code he wrote for the attack stole the compromised users' Twitter credentials via a netcat command. The Jester claims he checked these credentials against a list of known targets before stealing any data. He had a list of enemies:
Here's a very SMALL sample of the much longer list: @alemarahweb,@HSMPress @AnonymousIRC, @wikileaks, @anonyops, @barretbrownlol, @DiscordiAnon etc etc etc
He noted anyone on his "shit-list" was left unscathed:
EVERYONE else without exception was left totally 'untouched' so to speak. This was a Proof of Concept QR-Code based operation against known bad guys, the same bad guys that leak YOUR information, steal YOUR CC nums, and engage in terror plots around the world. I do not feel sorry for them. In the interests of convenience I will be taking the liberty of uploading the captured bad-guy data in a signed PGP encrypted file to a suitable location very soon. How's that for 'lulz'?
The Jester this week posted a 143.08 MB text file, which he refers to as the "resulting raw dump of the verbose output log from this exercise," on MediaFire. It's encrypted with his PGP Public key, so there's no way of telling if the contents are what he claims they are, or if he's just trolling.
Rhode Island State Representative Dan Gordon was supposedly one of the victims. Gordon made it onto The Jester's "shit-list" for a tweet that reference Anonymous, which The Jester interpreted as approving of the hacktivist group. Gordon reacted angrily to The Jester's jeers on Twitter. He threatened to report the hacker to authorities for offences ranging from threatening a state official to hacking the mobile phone of an elected politician. Later though, Gordon said he had not scanned the QR code and thus could not possibly have been hacked.
Here are some tweets from The Jester's account in regards to this particular attack:
Curiosity Pwned the Cat: ‘Curiosity is lying in wait for every secret’. – Ralph Waldo Emerson At the beginning ... http://t.co/IuLZUb0w Received reports that my latest blog post triggered AVG, I have removed the exploit source & used screen dumps instead https://t.co/36QVViTP RT @swordandsalt: @th3j35t3r "Never interrupt your enemy when he is making a mistake." - Napoleon https://t.co/36QVViTP So @repdangordon WAS on 'shit list' & scanned QR. Why's he on the list: http://storify.com/dailydot/state-rep-reps-anonymous & he's friends w/this guy: http://th3j35t3r.wordpress.com/2011/08/21/if-ya-cant-beat-em-make-some-shit-up-lmao/#dick @repdangordon so you & some anon are trying to find me? Man, you are not gonna come out of this looking good Dan http://t.co/87UO8JPd @RepDanGordon @FBIPressOffice I merely stated u were on the list, u seem awful jittery. U need to calm down >> ;-) http://t.co/87UO8JPd @RepDanGordon Go away Dan, I'm sick of helping u embarrass urself. I merely said u were on the list. Hey>> http://www.cbsnews.com/2100-250_162-20111212.html #stolenvalor @repdangordon be advised, when u file ur complaint to feds, they ARE going need ur cell for forensics to determine IF I hacked u at all ;-( @repdangordon >> http://www.blogtalkradio.com/johntiessen/2012/02/23/the-strait-truth-with-your-host-john-tiessen-1/scrub/0 << chatting="" about="" #anonymous="" with="" his="" friend="" @johntiessen="" <<="" remember="" him?="">> http://th3j35t3r.wordpress.com/2011/08/21/if-ya-cant-beat-em-make-some-shit-up-lmao/#dick @repdangordon - I told you before, all I stated was that your name was on the list. You have since proved why. http://pastebin.com/et1LnCAL @repdangordon creates a new twitter under @Rep_gordon in fail attempt to back pedal, however we all know who you are >> #Checkmate >>> https://twitter.com/#!/th3j35t3r/status/179661949087399937 <<< I'll="" make="" you="" famous="">>> https://www.youtube.com/watch?v=mOzOdj7JmfE #anonymous
It's unclear whether the clever attack actually worked. Maybe The Jester is just trying to rile up his enemies (it certainly worked for Gordon). We won't know until he releases the password to the aforementioned file, if ever.
See also: