Hackers pounce on just-patched Windows Media vulnerability

If you haven't gotten around to patching that Windows Media Player vulnerability fixed in the last Microsoft Patch Tuesday batch, you might want to immediately fire up Windows Update.
Just a few weeks after Microsoft shippedMS12-004, a “critical” bulletin with fixes for two serious flaws in the way Windows Media handles certain media files, hackers have pounced and are exploiting this issue to plant malware on unpatched computers.
According to a warning from Trend Micro, the in-the-wild attacks are being launched via web sites rigged with booby-trapped Windows media files.
Trend Micro said the infection vector is a malicious HTML which exploits the vulnerability by using two components that are also hosted on the same domain. The two files are: a MIDI file and a JavaScript, the company said.
[ SEE: 'Critical' Windows Media flaws put millions at risk ]
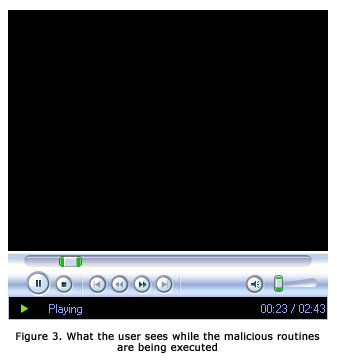
The end result is a malicious Trojan with rootkit capabilities. The attack happens silently in the background and all the user sees is a blank WMP application playing a file.Researchers at IBM ISS are also reporting increased chatter around the simplicity of exploiting this particular vulnerability:
In addition to the appearance of live exploitation, detailed discussion of the vulnerability details and methods of exploitation have been seen. The relatively low complexity of locating the vulnerability will doubtlessly lead to more malware targeting it.
This particular threat doesn't appear to be widespread at the moment but it's very likely that this bug could be fitted into popular exploit kits so it's important to apply this patch as soon as possible.