Inside BBC's Chimera botnet
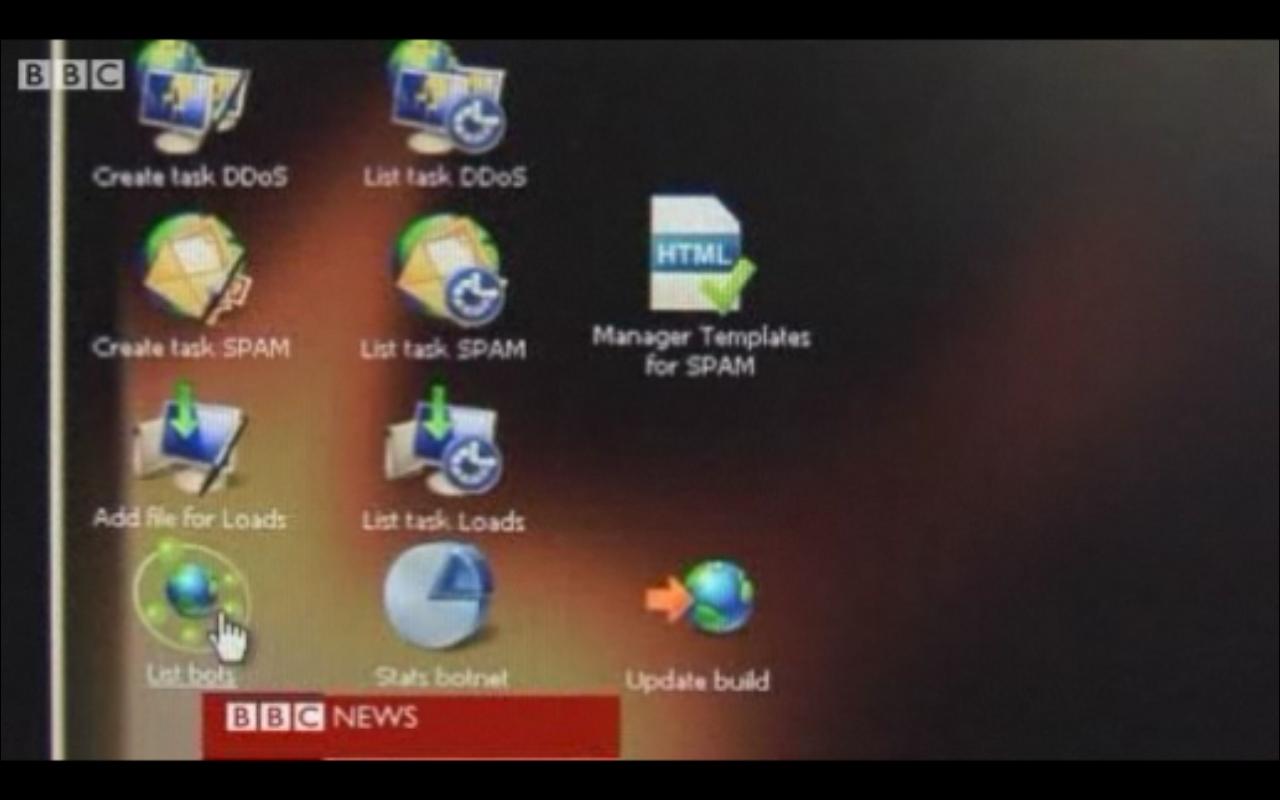
Until now. Let's take a peek inside the BBC "Chimera Botnet" offered for rent by a Russian Cybercrime-as-a-service (CaaS) vendor.
The Chimera botnet is courtesy of a Russian vendor developing web applications and backend systems for botnets, with a particular emphasis on coding malware for hire. Some of their most notable (public) releases include performance-boosting modifications within the Zeus crimeware kit, the introduction of a carding-theme within the kit (now an inseparable part of all the new versions), and integrating a MP3-player/online radio feature within the crimeware kit. The managed service offers two versions in a typical modular-malware fashion in this case for spamming and launching DDoS attacks, with the backend's interface exclusively based on the ExtJS AJAX framework, with the malware itself compatible with Windows SP sp1/2/3, and Windows Vista with the authors claiming it will run as an authorized application.
- Go through related Cybercrime-as-a-Service posts: The Neosploit cybercrime group abandons its web malware exploitation kit; Cybercriminals release Christmas themed web malware exploitation kit; Crimeware tracking service hit by a DDoS attack
How much did the BBC pay for access to the managed botnet, and what are the chances that the sellers are involved in a countless number of hardcore cybercriminal activities? Interestingly, the (now down) vendor's site isn't exclusively offering the 20k infected hosts that the BBC purchases, thereby leaving the possibility for what may look like an overpriced deal. However, a price of $400 for a particular managed malware binary is cited, with the size of botnet changing proportionally with the vendor's malware campaigns circulating in the wild.
The disturbing part with such "malware for hire" and "botnets for rent" services is their emphasis on standardization which results in efficiencies and efficiencies themselves in cost-effective scalability. For instance, asked by a customer whether or not their backend can handle more than 50k of infected hosts before requesting a customer-tailored interface, the vendor responds that the last big botnet that they ported costing of 1.2 million hosts was working "just fine".
The Chimera botnet's vendor is currently in a cover-up mode, monitoring of their releases would continue.