Jeff Jones (err Microsoft): Vista more secure than everything

Microsoft's Jeff Jones is at it again with a report claiming that Vista is more secure than its predecessor--XP--and every other modern operating system out there.
I know what you're going to say--Jones is a blowhard. He says what Microsoft wants to say but doesn't so the company appears above the fray. Any number can be twisted. He's not exactly objective. In fact, I'm inclined to agree with you. But here's the report anyway. Why give Jones a podium since he's obviously pro-Microsoft? You can still learn from people that have an obvious stake in their analysis. To me it's no different than an analyst disclosing a position in a stock. As long as it's disclosed I'll give it a shot.
In a blog post, Jones, security strategy director in Microsoft's Trustworthy Computing group, provides the PDF report. It uses a one-year take since from Nov. 2006 to Nov. 2007 since that's when Vista shipped to business customers (whether these folks actually installed Vista is another argument entirely).
Some key takeaways:
Jones (previous reports) says Vista is more secure than XP and Microsoft has its patching act together. Jones writes: "The results of the analysis show that Windows Vista has an improved security vulnerability profile over its predecessor. Analysis of security updates also shows that Microsoft improvements to the security update process and development process have reduced the impact of security updates to Windows administrators significantly compared to its predecessor, Windows XP."
I'm inclined to agree with that--even though I'm still on XP. Whether Vista is more secure will be determined over time. But Microsoft has improved its security update process since XP's heyday.
The methodology and the metric dance. It sure would be swell if there were one uber metric to measure security. There isn't and Jones cops to that. He notes in his report:
If it was possible to measure "security" in one metric, it would have to encompass a complex combination of factors including (but not limited to) the software quality, administrative controls, physical controls, and much more - and even then, it would all be in the context of whatever security policy was defined for the systems in question. So, this is not an analysis of "the security". I don't look at protective mechanisms and see how they might protect in certain scenarios. Nor do I look at security features and see how they might enable better privacy or help secure business process. And I certainly don't look at how easy it is to manage the security policy for these products. Is there anything in this analysis which will prove one piece of software is "more secure" than another? No, that is not my intention.
Nevertheless, Jones gives you metrics measuring security. He uses a vulnerability analysis, tosses in some caveats and moves along with CVE counts. Jones' report oddly looks a lot like George Ou's report last month when he tried to compare IE and Firefox. And since most of you gave poor George hell I assume you'll disapprove of Jones' counts too.
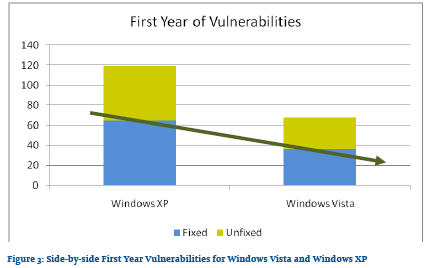
Jones lets the charts do the talking on Windows vs. XP.
Windows XP vs. Vista.
And the event roundup comparing XP and Vista. Some of the patch events are due to a more regularly monthly update schedule.
After that warmup comes the OS comparisons. Jones compares Red Hat Enterprise Linux, Ubuntu and the Mac OS X 10.4. I'll provide the chart to keep it simple, but you should read through the actual analysis in the PDF. It's an interesting take even though you may beg to differ.
And.