Major career web sites hit by spammers attack
What is the future of spamming next to managed spamming appliances, like the ones already offered for use on demand?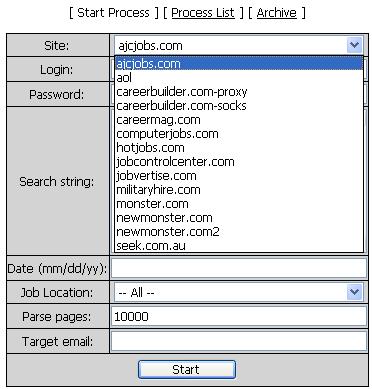
Email harvesting has been around since the early days of spamming, when the handy point-n-click mailto made it possible for the first databases of harvested emails to appear. Nowadays, these lists either come as a commodity, namely, they're free, or as a bargain for enticing the buyer of a particular underground good or service into buying it, and receive the list as a bonus. Recently, spammers, phishers and malware authors, started diversifying their harvested databases that would be later on used as hit lists for spam and malware campaigns, from the usual emails, to instant messaging screen names, Skype usernames, and even YouTube user names. In fact, the problem of spammers diversifying their hit list building approaches is so prolific, that successful initiatives such as the Project Honeypot aiming to proactively detect such email harvesters and limit their reach, would need to diversify their distributed aggregation approaches in the long term, to include many other ways in which spammers are harvesting "contact points" on their watch list.
Key summary points :
- the personal information harvesting tool comes with a customer service, which would provide the buyer with a custom module for any other web site included for the price of $100, in between providing accounts at that site and lists of proxy/socks hosts to be used, and therefore speaks for a decent degree of customerization
- the tool is entirely efficiency centered, namely, it allows multiple harvesting threads which in combination with several different socks/proxy hosts used can fetch and parse a huge number of pages in the shortest possible time frame
- the service has a built-in proxy/socks functionality, allowing the spammers to forward the responsibility for the harvesting process to the owner of the proxy/socks which in most cases is a malware infected PC used as a stepping stone for committing other illegal acts
- one of the main differentiation factors of this tool compared to the many other average email harvesters, is the customization achieved, namely the spammer can harvest only emails of people living in a certain country, city, working a specific profession, having studied in a particular school, or having worked in a particular company in the past, spoken language, possession of a security clearance, as you can see in the attached screen shots the variables for coming up with unique and highly targeted spamming lists fully match the variables for searching on a per job site basis
- the possibilities for targeted spamming and malware attacks here are enormous given the quality of the harvested data, which compared to the plain simple email addresses spammers harvest, a situation where they have no idea about any other personal details of the email owner, in this security incident, the information in all of its authenticity and quality is provided by legitimate job seekers wanting to dazzle their future employers by providing them with as much information as possible
- the tool relies on the already registered accounts at these sites, whenever it cannot recognize the CAPTCHA, and according to the description it can recognize the CAPTCHA of a single career site only, CAPTCHA images are parsed within the interface per session, so even if the CAPTCHA for a certain site cannot be automatically recognized, the spammer is verifying it successfully, thereby gaining access inside the portal as a legitimately authenticated job seeker
- as it appears from the obtained log files, the tool has already been actively harvesting the job sites
Description of the do-it-yourself email harvesting tool:
"Your attention is invited to product-collector e-mails within web resources. By purchasing our product, you get free updates for life, the opportunity to use our hosting for the collection of e-mails. Many have already chosen our product and we are grateful. Product Price: $ 600 Help with the installation - for free. It is possible to write custom modules - normal price is $ 100 and the availability of the resource account for which you want to write a module. PHP Mailers for direct spamming come as a gift."
Sites targeted and included in the web application :
Ajcjobs.com; CareerBuilder.com; CareerMag.com; ComputerJobs.com; HotJobs.com; JobControlCenter.com; Jobvertise.com; MilitaryHire.com; Monster.com; Seek.com.au
With the increasing information sharing between security vendors, non-profit
Out there right now, there's a legitimately registered user, whose access to a site is efficiently abused part of an illegal operation. It could happen at any site, at any time, not necessarily job sites only given that a custom module for any other site could be build as well. However, job sites were originally targeted in this incident because of the quality and easy to aggregate, personal information.
Here are several more related screen shots showcasing the rest of the tool's option.
A sample output in the form of full name and the associated email :
The variables to set before harvesting the email addresses :
Other variables for a specific career site :
Sample log file of the process :
The trend of obtaining high quality personal data from business social networks is only starting to take place.