Mass SQL injection attack leads to scareware
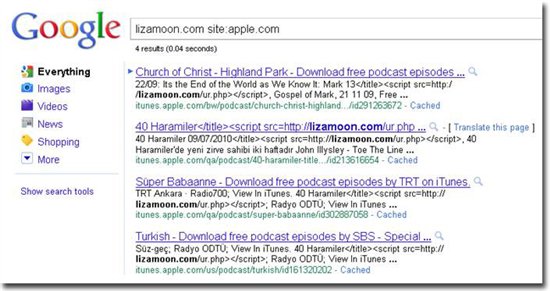
Security researchers from WebSense have detected a mass SQL injection attack (hxxp://lizamoon.com; 58,300 affected pages), which the cybercriminals monetize through scareware, also known as fake security software. The attack has also affected several iTunes web pages.
UPDATED: Additional information regarding the campaign is available: Dissecting the Massive SQL Injection Attack Serving Scareware.
More details:
The way iTunes works is that it downloads RSS/XML feeds from the publisher to update the podcast and list of available episodes. We believe that these RSS/XML feeds have been compromised with the injected code. The good thing is that iTunes encodes the script tags, which means that the script doesn't execute on the user's computer. So good job, Apple.The URL that is injected is unavailable right now, but the server is still up and running, so that could change at any time. While it was up, the script contained simple JavaScript code that redirected the user to a well-known Rogue AV site: hxxp://defender-uqko.in. That site is also unavailable right now, so we don't have the actual binary analysis information available yet.
From the perspective of the attacker, mass SQL injection attacks are highly beneficial from a blackhat SEO (blackhat search engine optimization) perspective, as they hijack both the affected web site's page rank, including the SEO-friendly content that comes with it. Compared to malvertising attacks, mass SQL injection attacks have declined in recent months, indicating a migration trend towards shorter, but more traffic-intensive windows of opportunities for malicious attackers to take advantage of thanks to malvertising.
Users are advised to use NoScript, as well as go through the Ultimate Guide to Scareware Protection.
See also: