Microsoft's anti-exploit toolkit can help mitigate PDF zero-day attacks

Microsoft is pushing its new Enhanced Mitigation Experience Toolkit (EMET) as a temporary mitigation for the ongoing attacks against a zero-day vulnerability in Adobe's PDF Reader/Acrobat products.
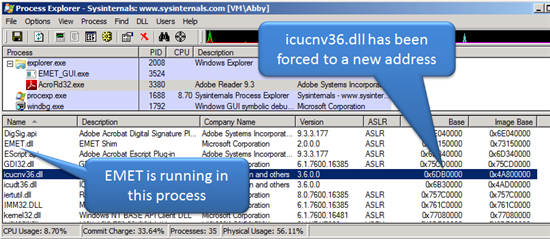
The EMET utility, which effectively backports anti-exploit mitigations like ASLR (Address Space Layout Randomization) and DEP (Data Execution Prevention) to older versions of Windows, would force the relocation of non ASLR-aware DLLs in Adobe's products.
[ Microsoft ships anti-exploit tool for IT admins ]
Adobe Reader and Acrobat products ship with a DLL (icucnv36.dll) that doesn't have ASLR turned on.Without ASLR, this DLL is always going to be loaded at a predictable address and can be leverage by an exploit.
However, on Windows 7, Windows Vista, Windows Server 2008 R2, and Windows Server 2008, the DLL would be forced into a new address.
The exploit will then fail to use ROP successfully since it is expecting the DLL to be at a predictable location.
[ New Adobe PDF zero-day under attack ]
As previously reported, the zero-day attacks against Adobe PDF Reader/Acrobat includes the use of clever techniques to bypass anti-exploit roadblocks in Windows and a signed digital certificate belonging to a U.S. credit union.Adobe has released an alert to confirm the vulnerability and active attacks and now confirms that Microsoft's EMET can be used as a temporary mitigation.
EMET supports both 32- and 64-bit applications and activates specific protection mechanisms in compiled binaries. It adds the following mitigations to applications that do not support them natively:
- Structured Error Handling Overwrite Protection (SEHOP) prevents Structured Exception Handling (SEH) overwrite exploitation by performing SEH chain validation.
- Dynamic Data Execution Prevention marks portions of a process’s memory non-executable, making it difficult to exploit memory corruption vulnerabilities.
- NULL page allocation allocates the first page of memory before program initialization and blocks attackers from taking advantage of NULL references in user mode.
- Heap Spray Allocation pre-allocates memory addresses to block common attacks that fill a process’s heap with specially crafted content.
- Mandatory address space layout randomization (ASLR), as well as non-ASLR-aware modules on Windows Vista, Windows Server 2008 and Windows 7.
- Export address table (EAT) uses hardware breakpoints to filter access to the EAT of kernel32.dll and ntdll.dll, blocks access if the instruction pointer is not inside a module, and breaks current common metasploit shellcodes.