Report: Hackers swipe FTP server credentials using SaaS

Finjan said it has uncovered a database with more than 8,700 FTP account credentials--user name, password and server address--that allow hackers to compromise security and deliver malware as a service.
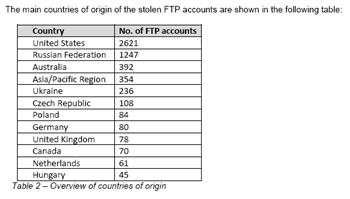
What's notable about this development is that hackers are using a software as a service (SaaS) model to deliver applications that are designed to abuse and trade FTP accounts. According to Finjan, this database may be the first use of SaaS for something other than legitimate means. Maybe we could call it HaaS: Hacking as a service.
Here's a model of how this threat works:
Finjan said its researchers managed to obtain some of the attacker’s server side components to reach the following conclusions:
- A standalone application was found at the backend of the malicious server that enables behind-the-scene information trading.
- The methodology used for attacks supports multiple “users” (attackers), mimicking a SaaS (Software as a Service) model.